
- jaro education
- 3, May 2024
- 12:21 pm
The concept of cybersecurity is constantly evolving as it is essential for protecting digital assets and infrastructures from various cyber-attacks. In the field of cybersecurity, two strategies have gained popularity: defensive and offensive cybersecurity. The major difference between offensive and defensive strategy is that the goal of defensive cybersecurity is to shield data, networks, and systems against hostile activity, unauthorized access, and security breaches. It also involves identifying and reducing vulnerabilities by incorporating strong security measures such as intrusion detection systems, firewalls, encryption, and many more.
Conversely, offensive cybersecurity, which is also referred to as penetration testing or ethical hacking, involves proactively locating and taking advantage of security holes in a system. By mimicking actual cyberattacks, this method enables organizations to assess their security posture and adjust their defenses accordingly. These two tactics must work together to build a strong foundation of cybersecurity architecture, as it is necessary to protect against evolving cyber threats. However, there is a lot more to these two strategies, which will be a matter of discussion in this blog.
What is Cybersecurity
As the guardian of the digital age, cybersecurity is responsible for protecting the ever-growing network of interconnected systems against a constant barrage of attacks. In other words, cybersecurity is recognized as a process of protecting computers, networks, servers, cellphones, other electronic systems, and data against hostile intrusions that pose the threat of manipulating the data along with destroying the system. It is often referred to as electronic information security or information technology security.
Table of Contents
However, one cannot emphasize how crucial cybersecurity is at a time when digital transformation propels innovation and connectedness. The significance of cybersecurity ensures the availability, integrity, and confidentiality of digital assets grows more and more crucial as technology develops and cyber-attacks become more sophisticated. In light of this, everyone, including individuals, companies, and governments, must understand and put into practice effective cybersecurity measures as we transverse into the intricately linked and complicated digital world.
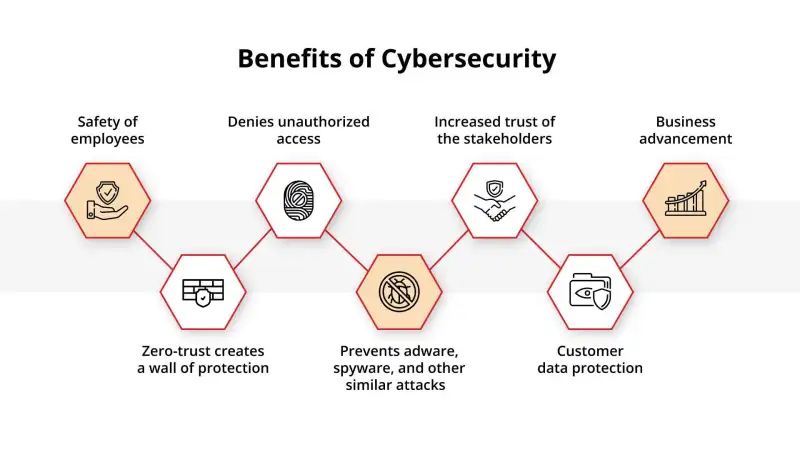
Benefits of Cybersecurity
Other than protecting digital assets from vicious cyberattacks, some additional benefits are linked with cybersecurity. Let us now take a look at the several benefits of cyberattacks:
*payatu.com
- For corporations or individual consumers, data is considered to be of the highest importance as it contains confidential information. For such situations, cybersecurity creates a shield that protects the data from internal dangers, whether unintentional or deliberate. Thus, consumers can use the internet whenever they need to without worrying about data breaches.
- Cybercriminals can get around data security measures by developing new techniques to attack data. This can be considered as one of the negative impacts of technological advancements. Hence, to protect the firms from any malicious data breach, entrepreneurs can install certain cybersecurity measures. Not only would it help to protect the data, but it would also enhance the productivity of the firms.
- One of the most significant advantages of cybersecurity is that it can reduce monetary losses for consumers, companies, and organizations. By incorporating strong cybersecurity measures, organizations can mitigate major financial losses that may occur due to certain data breaches.
- Cybersecurity offers businesses complete online safety. This provides the workers with freedom, security, and flexibility while using the internet.
Defensive Cybersecurity
The first line of defense against a wide range of cyber threats that aim to compromise digital assets, networks, and systems is defensive cybersecurity. Its main goal is to safeguard these resources from hostile activity, illegal access, and data breaches. A variety of preventative actions are included in defensive cybersecurity, such as the installation of intrusion detection systems, firewalls, encryption methods, and frequent security upgrades.
Defensive Cybersecurity seeks to reduce risks and protect sensitive data and the operations of organizations by continuously monitoring, identifying, and reacting to any attacks. Adopting strong defensive cybersecurity tactics is crucial to ensure the longevity and security of the digital infrastructures of an organization, especially in this interconnected world of technology. These strategies are important for safeguarding valuable information due to the ever-evolving nature of cyber attacks in the landscape of digital transformation.
Offensive Cybersecurity
Compared to defensive cybersecurity, offensive cybersecurity is an aggressive approach to cybersecurity that aims to find and take advantage of weaknesses in the networks, applications, and systems of an organization. Offensive cybersecurity simulates actual cyberattacks to evaluate the efficacy of current security measures, in contrast to defensive cybersecurity, which concentrates on bolstering defenses and reducing risks. By emulating the attitude and methods of malevolent hackers, offensive cybersecurity experts find vulnerabilities before enemies can take advantage of them.
By taking a proactive stance, companies may fortify their defenses, prioritize security investments, and efficiently reduce risks. In the never-ending arms race against cyber threats, offensive cybersecurity is essential to an organization’s ability to stay one step ahead and improve its overall security posture and resilience.
Difference Between Offensive and Defensive Cybersecurity
Both offensive and defensive cybersecurity strategies hold equal importance in protecting digital systems from any attacks on the digital world. However, there are some significant differences between offensive and defensive strategies that set them apart from each other.
Here are some of the major points of difference between both of these cybersecurity strategies:
- Initiatives in the field of offensive security are typically started by groups or organizations that wish to assess the security of their own or other people’s systems. However, in the case of defensive security, an organization or a person launches this security measure to check the reaction to a perceived danger or to stop an attack before it begins to unfold.
- Red teaming, penetration testing, and vulnerability assessment are examples of offensive security approaches. Firewall setup, prevention systems, event management (SIEM), and many more are some of the few examples of defensive security measures.
- Professionals who specialize in offensive security may possess a more specialized skill set since they work in a particular area of security. Professionals in defensive security usually possess a broader comprehension of security concepts and procedures.
- Testing a system or network’s security is a common goal of offensive security. The goal of defensive security is to safeguard a company’s infrastructure and assets.
- In offensive security, a system is seen from the standpoint of an attacker, and methods of compromise are sought. By approaching a system from the standpoint of a defender, defensive security aims to find and fix any possible weaknesses.
- Custom malware and exploit frameworks are two examples of tools and approaches that are often used in offensive security. Defensive security does not utilize any of the tools implemented in offensive cybersecurity.
- Offensive security’s main goal is frequently to identify and exploit certain weaknesses. Defensive security’s main emphasis is on implementing a wide variety of controls to guard against a broad spectrum of potential threats.
- If offensive security actions are carried out without the system owner’s permission, they may be deemed unethical. Activities related to defensive security are typically seen as moral.
- The goal of offensive security is to test and strengthen a system’s security by proactively targeting and taking advantage of flaws. The main goals of defensive security are to thwart and counterattack.
- Because it’s frequently implemented in reaction to a particular attack or vulnerability, offensive security is often more reactive. As it focuses on averting assaults before they happen, defensive security is usually more proactive.
Defensive Cybersecurity Strategies
Let us take a look at various defensive cybersecurity measures that prevent the attack of major cyber threats against digital assets and systems:
- The discipline of IT security management safeguards an organization’s information systems, networks, and assets against both internal and external cyber threats.
- The term “cloud security” describes the grouping of regulations, tools, strategies, and procedures employed to safeguard an organization’s cloud computing infrastructure, data, apps, and services.
- A simple and common defensive strategy is installing access controls. This strategy can help entrepreneurs manage the authorization of the company’s systems and assets. Access controls can be of various types, including biometric scans, passwords, and usernames.
- Networks can be divided into smaller sections, or subnetworks, to manage access and traffic flow. This approach further prevents malware from spreading and improves overall network security.
- To lessen the effects of ransomware attacks, data breaches, and system failures, regular backup procedures and strong data recovery procedures should be established. This will guarantee the availability and integrity of crucial data and systems.
Offensive Cybersecurity Strategies
Often, offensive cybersecurity measures have proven to be more beneficial than defensive cybersecurity strategies. Below are some of the popular strategies that are implemented under offensive security:
- One of the most popular strategies is red team operations, which mimic extensive cyberattacks on an organization’s network, frequently testing incident response skills and breach defenses.
- An exploitation technique involves providing attackers with a major edge by making use of previously undiscovered flaws in hardware or software that have not been fixed or addressed.
- One kind of ethical hacking that is used to identify vulnerabilities in a company’s network is called a penetration test.
- A range of instruments and strategies are employed in vulnerability scanning to look for known security threats and weaknesses in a network. By using vulnerability scanning, the entrepreneurs may find and evaluate the risk connected to the weaknesses in the network. This technique helps in prioritizing which security flaws need to be fixed as soon as possible.
- A manipulation method known as “social engineering” makes use of interpersonal relationships to obtain and plunder assets, other goods, and private information. Ethical hackers employ this method in offensive cybersecurity to identify and discourage malevolent behavior.
Conclusion
In the current digital environment, both offensive and defensive cybersecurity tactics are essential parts of a whole security architecture. Defensive cybersecurity concentrates on protecting networks, systems, and data from possible attacks, whereas offensive cybersecurity actively seeks out and takes advantage of weaknesses to bolster defenses. There exist some differences between offensive and defensive strategies. Still, when combined, these tactics create a flexible and proactive strategy for cybersecurity that helps businesses successfully reduce risks and keep ahead of ever-changing threats. Organizations may strengthen their security stance, safeguard important resources, and guarantee resilience against the dynamic threat environment of the digital era by adopting a well-rounded strategy that combines offensive and defensive techniques.
If you want to know more about the evolving concept of cybersecurity and its various strategies, then you must enroll in the Executive Programme in Artificial Intelligence and Cybers Security for Organizations [EPAI&CSO] by IIM Indore. Specially designed for organizational leaders, this innovative program offers a unique combination of theoretical knowledge and practical applications, having been painstakingly constructed by renowned industry professionals and academic luminaries. This course will equip the participants with the sophisticated AI methodologies, cyber threat intelligence, risk management tactics, and creative defense mechanisms through an immersive learning experience, that can help them protect organizations against new cyber dangers.









