Advanced Professional Certification Programme in Cybersecurity and Ethical hacking
—E&ICT, IIT Guwahati
Programme Overview
Combat cyber heist challenges and eliminate security threats. Upskill and transform into well-suited and skilled Cyber Security Experts by learning to prevent organisations’ cybersecurity mesh by developing security architecture with India’s top IIT. Unlock fundamental concepts in cybersecurity, ethical hacking, and their applications to reimagine organisational goals. Explore IIT’s cutting-edge curriculum, which includes a mix of theory, capstone project, case-based learning, and much more. Join E&ICT’s, IIT Guwahati’s revolutionary Advanced Professional Certification Programme in Cybersecurity and Ethical hacking to help you establish a benchmark in your cybersecurity career.
Programme Highlights

Certificate of Completion from E&ICT, IIT Guwahati

Live Classes by Highly Experienced Faculty Members from IITs & Industry Experts

3 Days of Intensive Campus Immersion Modules

Pedagogy includes Case Discussions
Hands on Training and Project Work

Peer-to-peer Learning and Industry Experts Mentorship
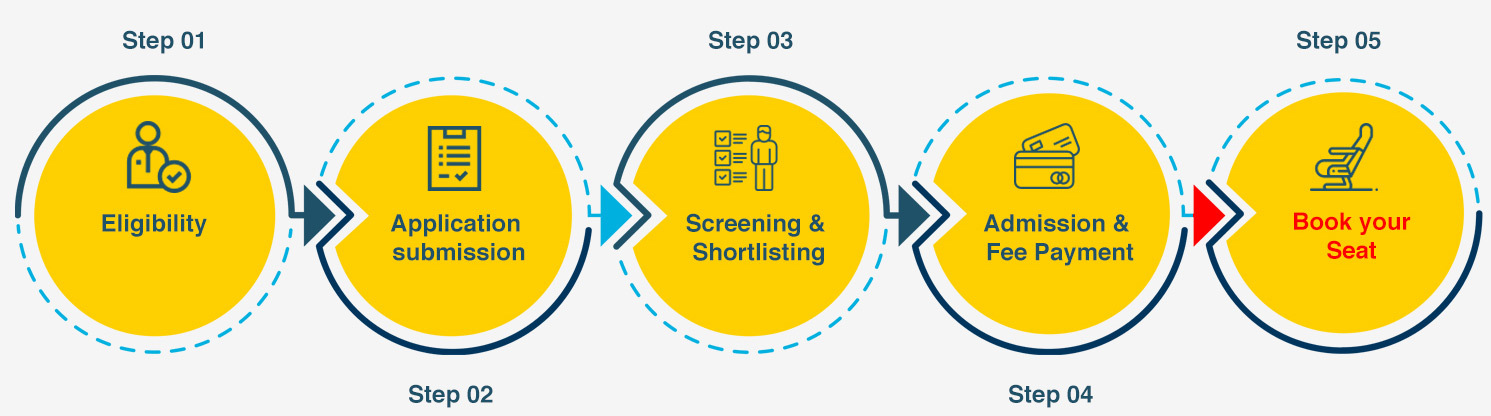
Admission Criteria
Eligibility Criteria
- Graduates (10+2+3 or equivalent) in any discipline recognised by UGC/AICTE with minimum 50% aggregate marks at either UG/PG level.
- Minimum 2 years of work experience is desirable.
Syllabus Breakdown
- Python Environment Setup and Essentials
- Python Language Basic Constructs
- Introduction to Linux and File Management
- What is Cyber Security
- Overview
- Need and Importance
- Different Verticals
- Introduction to Kali Linux
- Services in Kali (HTTP, SSH)
- Wget, curl, grep, awk, tail, head, watch, find, locate
- Piping and Redirection
- Python and Bash Scripting
- Netcat, Socat, Powercat, Powershell, Wireshark, tcpdump
- Note taking
- Security Controls
- Networking Concepts
- Traffic Analysis
- Packet Analyzers
- Sniffers
- Firewalls
- SIEM
- VLAN
- VPN
- Understand the Basic Concepts of Security
- Information and Event
- Management (SIEM)
- Discuss the Different SIEM Solutions
- Understand the SIEM Deployment
- Learn Different Use Case Examples for Application
- Level Incident Detection
- Learn Different Use Case Examples for Insider Incident Detection
- Learn Different Use Case Examples for Network Level Incident Detection
- Learn Different Use Case Examples for Host Level Incident Detection
- Learn Different Use Case Examples for Compliance
- Understand the Concept of Handling Alert Triaging and Analysis
- Understand the SOC Fundamentals
- Discuss the Components of SOC: People, Processes and Technology
- Understand the Implementation of SOC
- Logical/Physical Access to Assets Management
- Authentication and Identification Management
- Integrating Identity as a Third-Party Service
- Mechanism of Authorization
- Provisioning Life Cycle’s Identity and Access
- OWASP Tools and Methodologies
- Insecure Deserialization
- Clickjacking
- Black Box Testing
- White Box Testing
- Fuzzing
- Cryptograph
- Symmetric/Asymmetric Cryptography
- Hashing
- Digital Signatures
- API Security
- Patch Management
- Types
- Ransomware
- Detection
- Analysis
- Introduction
- Footprinting and Reconnaissance
- Scanning Networks
- Enumeration
- Vulnerability Analysis
- System Hacking
- Sniffing
- Social Engineering
- Denial-of-Service
- Session Hijacking
- Evading IDS
- Firewalls and Honeypots
- Hacking Web Servers
- SQL Injection
- Hacking – Wireless Networks
- Mobile Platforms
- IoT
- Infrastructure Security: Network level security, Host level security, Application-level security
- Data security and Storage: Data privacy and security Issues, Jurisdictional issues raised by Data location
- Access Control
- Trust, Reputation, Risk
- Authentication in cloud computing, Client access in cloud, Cloud contracting Model, Commercial and business considerations
- Security Controls for The Development Environment
- Life Cycle Security
- Impact of Acquired Software Security
- Effectiveness of Software Security
In this module, you will learn how to prevent a web application from being hacked as well as what key points to be considered for making a web application secure. This capstone project will give you exposure to both the blue team and red team work profile and help you gain exposure on both sides.
*The above given is an indicative list of modules and is subject to change as per E&ICT, IIT Guwahati’s discretion.
About IIT Guwahati

About E&ICT Academy
7th
as per NIRF 2022
41st
globally in the ‘Research Citations per Faculty’
395th
Overall in the QS World University Rankings 2022
Learn Live From Top IIT Guwahati’s Faculty

Associate Dean (Administration),
Indian Institute of Information Technology Guwahati
PhD and MTech degrees from IIT Guwahati, in Computer Science and Engineering


*The above list of faculties is indicative and partial and is subject to change or update as per E&ICT, IIT Guwahati’s discretion.
Programme Certification

Fee Structure
(Payable – April 10th 2023)
(Payable – July 10th 2023)
The Jaro Advantage

- Unparalleled career guidance and support
- Dedicated student support
- Immersive and lifelong learning experiences

- Learn from the best-suited academic, faculty, and industry mentors
- Be a part of discussions and forums for enhanced learning
- Leverage peer-to-peer learning experience

- Alumni Network of 3,50,000+ Professionals
- Access to alumni events & other benefits
- Stay up to date with the latest insights from your alma mater
Jaro Expedite - Career Booster
Profile Building
Rigorously building the candidate’s profiles and resume scrutinizing their LinkedIn profiles. Jaro Education enables personalised feedback to boost overall virtual presence.
Resume Review
Moving forward with carefully curated resume reviews that ensures you are interview-ready for the workplace of tomorrow.
Placement Assistance
Get career assistance as per the profile and preferences. On average, get 5-6 job recommendations to enhance quality employment opportunities.
Career Enhancement Sessions
Bridging connectivity to link the best talent with organizations through eminent sessions from top-class industry speakers.
Note: E&ICT, IIT Guwahati or Jaro Education do not guarantee or promise you a job or advancement in your existing position. Career Services is simply provided as a service to help you manage your career in a proactive manner. Jaro Education provides the Career Services described here. E&ICT, IIT Guwahati is not involved in any way with the Career Services described above and offer no commitments.
Build 21st-Century Skill set to Gain Career Edge in the VUCA World
You’ll learn
- Design, develop, execute and evaluate secure software.
- Deep dive into the nuances of cyber security and ethical hacking.
- Detect & fix security issues in networks and computer systems to secure an IT infrastructure.
- Propose solutions, including development, modification and execution of incident response plans.
After completing the programme criterias, all eligible participants will be awarded with a certificate of completion by E&ICT, IIT Guwahati.
The Advanced Professional Certification Programme in Cybersecurity and Ethical hacking will be delivered in an engaging Direct to Device mode, allowing participants to immerse themselves in an enriching learning experience.
Here’s the minimum eligibility criteria for Advanced Professional Certification Programme in Cybersecurity and Ethical hacking :
- Graduates (10+2+3 or equivalent) in any UGC/AICTE-recognized discipline with a minimum of 50% aggregate marks at the UG/PG level.
- Must have a prior work experience of at least two years is required.
The total programme fee is INR 1,80,000/- + GST.
 Talk to our career expert: Ms. Prajwala Patil | +91 8976977832
Talk to our career expert: Ms. Prajwala Patil | +91 8976977832