
- jaro education
- 13, May 2024
- 4:44 pm
The process of preventing illegal entry, cyberattacks, and data breaches from occurring to digital resources, networks, and systems is called Cybersecurity management. In today’s interconnected world where organisations as well as individuals are highly dependent on technology, cybersecurity management performs a vital role by protecting sensitive data and guaranteeing the availability and integrity of digital resources. The entire cybersecurity management can be performed seamlessly by putting preventative measures like firewalls, encryption, and access restrictions into place and creating incident response plans to deal with possible attacks. To safeguard the data, reputation, and business operations, companies of all sizes must prioritise cybersecurity management as cyber threats continue to evolve with the rapid growth in technology.
Similar to how we defend our homes by locking our windows and doors, cybersecurity strengthens our online defences to guarantee our data is safe over the wide internet. In an increasingly linked world, it is the unseen barrier that secures our digital personal identities and financial transactions and maintains the required privacy in the digital world. Cybersecurity works diligently underneath the curtains to keep an individual’s interactions with the internet safe, secure, and worry-free. Hence, cybersecurity is recognised as the unestimated messiah of the digital age.
Key Principles of Cybersecurity
A collection of guidelines known as the Cyber Security Principles was created to help Internet
Table of Contents
users feel more secure when using the Internet. In the event of hostile security breaches or cyber threats, they defend and offer strategic advice. Here are some of the key principles of security:
Risk Management
Balancing opportunities and dangers with a sound risk management strategy can facilitate delivering the finest corporate objectives. By following this approach, an entrepreneur can ensure that the organisation’s technology, data, and systems are protected in the best possible way.
Monitoring
Maintaining and gathering documentation is crucial to comprehending the operation and utilisation of the organisation’s system. Records can be utilised to look into the source of risk in the event of any danger or possible security breach. By keeping an eye out for any odd behaviour, this monitoring procedure aids businesses in reducing security problems.
Asset Management
Developing and preserving the necessary knowledge about each asset in an organisation is the essence of asset management. It gradually gets harder to comprehend and maintain the technological data of all the assets with the increasing number of systems required for operating business operations. A thorough evaluation of the assets can reveal unpatched services, upgrades and replacements needed, and several other vulnerabilities that must be fixed to reduce the likelihood of cyberattacks.
Authorization
Data security involves taking appropriate precautions to shield data against unauthorised access, destruction, or alteration. Data protection must be maintained both in transit and at rest, and after usage, data must be properly destroyed or disposed of. This ensures that obsolete devices do not contain critical data.
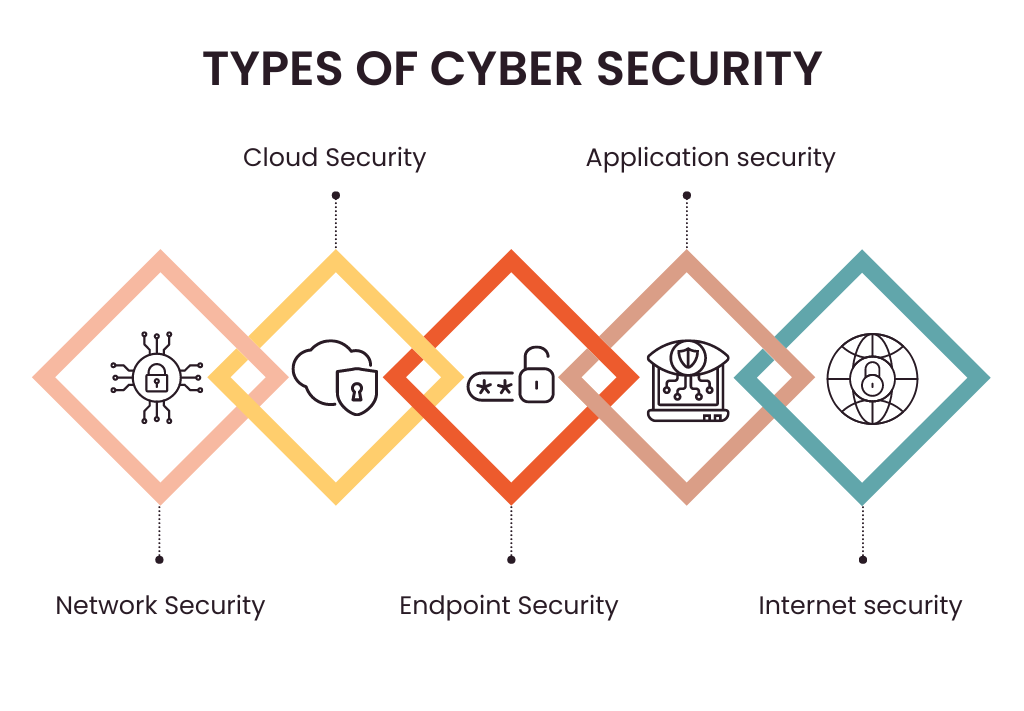
Types of Cybersecurity
Cybersecurity measures are used to defend digital systems against unintentional and malevolent attacks. Let us take a look at various types of cybersecurity measures:
Application Cybersecurity
Owing to the significant features of application security, several applications and their associated data cannot be used or accessed by unauthorised parties. Application security encompasses a wide range of cybersecurity solutions to help detect vulnerabilities during the design and development phases.
Mobile Security
Mobile security refers to various forms of cybersecurity that are used to keep mobile devices safe from illegal access and from being utilised as a means of network intrusion.
Cloud Security
Keeping cloud-based resources and services, such as data, apps, and infrastructure, is the main goal of cloud security. For the most part, cloud service providers and enterprises share responsibility for managing cloud security.
Operational Security
It refers to a broad range of cybersecurity procedures and technologies that safeguard confidential information by instituting access controls and keeping an eye out for anomalous behaviour that might indicate malicious activity.
End Point Security
All of the electronic device data is safeguarded by endpoint security. To defend networks against cyberattacks that leverage endpoints as ports of entry, it also includes other forms of cybersecurity.
Network Security Solutions
Devices and software that guard against events that cause illegal access or service interruptions are included in network security solutions. Risks that affect network hardware and software, such as operating systems and protocols, are monitored and addressed.
*theknowledgeacademy.com
What is Network Security?
Consider there is a virtual highway where data moves at the velocity of light and a busy system of highways connects multiple networks. In this gigantic maze, network security monitors this huge network system while keeping an eye out for possible threats that might be hiding behind cyberspace’s shadows. Network security is also responsible for guaranteeing the secure flow of information. Safeguarding the channels by which data travels, network security acts as an intangible force that fortifies the tunnels and bridges of the digital infrastructure. For trustworthy travellers, entry is granted, while unauthorised users are kept out by the digital locksmith.
Similar to how traffic signs and barriers control the flow of vehicles on the roadways, network security procedures and technological advances control data flow and avert traffic jams, collisions, and detours brought on by cyber threats. Network security offers stability, dependability, and peace of mind to both users and organisations by building a strong and secure foundation of internet connectivity in the rapidly growing field of cyberspace
Key Principles of Network Security
Three fundamental concepts are involved in network security: availability, integrity, and secrecy. One of these principles of network security may be more significant than the others, depending on its implementation and circumstances. Let us discuss in detail the key principles of security:
Integrity
Integrity has three objectives. The first objective is to prevent unauthorised users from changing information, while the second objective is to prevent unauthorised individuals from accidentally or unintentionally changing information. The third objective is to secure external and internal consistency. External consistency guarantees the consistency of the data kept in the database with the outside world, whereas internal consistency guarantees the consistency of internal data.
Availability
Availability guarantees that the data in a system and the network are accessible to authorised users promptly and without interruption. Additionally, there are a few crucial terms that fall under the domain of availability, such as follows:
The first term is authorisation, which defines the rights granted to a person or operation to utilise a computer resource. The second term is authentication, which confirms that the user’s claimed identity is valid with the help of a simple security measure such as a password. The third term talks about identification, which is a step taken before authentication. Under identification, a user professes their true identity to the system. Lastly, accountability defines a single person’s behaviour and activities inside a system and makes that person answerable for their deeds.
Confidentiality
The goal of confidentiality is to stop sensitive information from being disclosed without authorisation. This leak may have occurred accidentally as a result of someone handling the information carelessly or incompetently, or it may have been intentional as a result of someone cracking a cypher and reading the data.
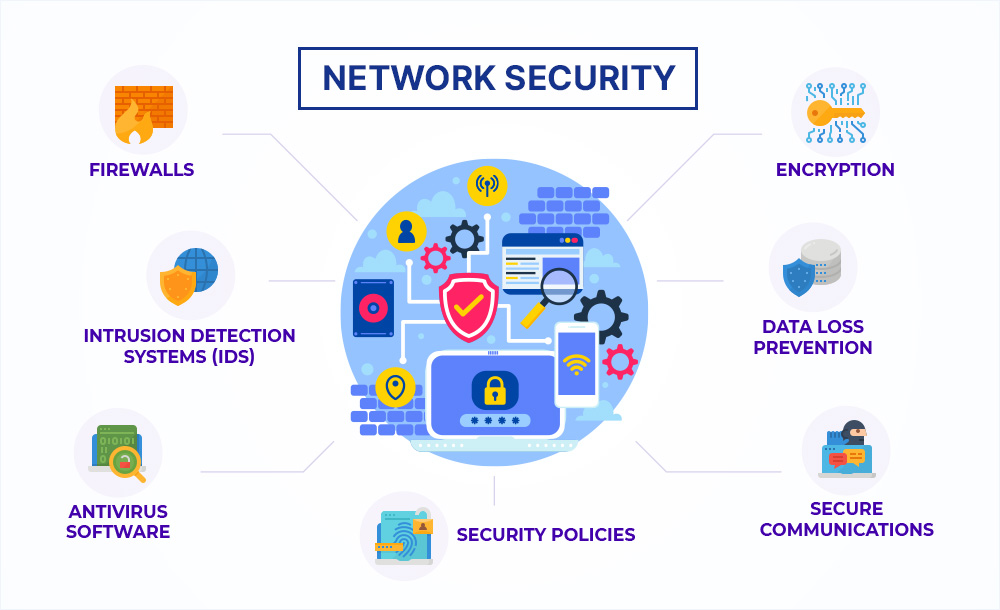
Types of Network Security
Network security guards against data theft, manipulation, and unauthorised access to networking infrastructure. Here are some of the multiple types of network security measures:
Email security
It is designed to stop users from inadvertently divulging private information or enabling unauthorised penetration into the network through an infected email. Emails containing potentially harmful threats will be warned about or blocked by this security feature.
Firewalls
Firewalls are used to filter network traffic. They regulate authorised entry within the network and try to stop and block unwanted internet traffic.
Access Control
To prevent unauthorised access and potential dangers, access control restricts the individuals, organisations, and devices that are allowed to use network applications and services.
Virtual Private Network
A virtual private network allows the use of multi-factor authentication (MFA), transmitted data encryption, and endpoint compliance while maintaining information integrity and privacy. Typically, telecommuters, extranet users, or mobile users can access the remote access VPN.
Behavioural Analytics
Security support staff must define normal behaviour for the users, apps, and network of a specific client to create a baseline from which abnormal behaviour may be distinguished. A security breach may frequently be indicated by typical signs of aberrant behaviour, which behavioural analytics software is intended to help detect.
Network Segmentation
When implementing policies, the entire work is made easier by dividing and classifying network traffic according to specific criteria. With the help of segmented networks, a few tasks, such as employee authorisation credential assignment and denial, are made simpler. It also ensures that no one accesses information they shouldn’t. Devices or incursions that may be compromised can also be isolated with the aid of segmentation.
*ir.com
Differences between Cybersecurity and Network Security
The implementation of both of these security measures is quite necessary to secure the sensitivity of stored information and protect digital assets from malicious cyber threats, as certain differences between cybersecurity and network security set them apart from each other. Here are some of the key dissimilarities of cybersecurity and network security:
| CYBERSECURITY | NETWORK SECURITY |
|---|---|
| 1. Securing digital data and protecting it from any dangerous content detected in cyberspace are collectively referred to as cybersecurity. | 1. One of the key elements of cyber security is network security, which safeguards every component found in the network space |
| 2. Addressing cyber threats in the online environment is the primary objective of cybersecurity. | 2. Protecting against network-specific threats, such as data exfiltration and attempted network intrusions, is the primary goal of network security. |
| 3. Compared to network security, cybersecurity incorporates numerous layers of protection by applying restricted security measures, including strict authorisation, encryption, access control, and many more. | 3. The goal of network security is to safeguard the network infrastructure by putting in place particular technologies and protocols, such as firewalls, network segmentation, and many more |
| 4. To safeguard digital property on multiple platforms and reduce cyber threats, cybersecurity specialists are in charge of creating and executing security policies, processes, and technology. | 4. To guarantee that the network infrastructure is resilient against cyberattacks and follows effective security practices, network security professionals concentrate on the creation, implementation, and upkeep of safety precautions that are exclusively designed for the network infrastructure. |
| 5. Cybersecurity aids in protecting private information against loss or improper usage. | 5. Network security can enhance a network's performance and dependability by avoiding restrictions and ensuring that resources are deployed properly. |
| 6. Cybersecurity defends against a variety of dangers, including ransomware, other online attacks, and more. | 6. Network security offers resistance against outside dangers such as hackers and malware |
| 7. Cybersecurity not only lessens the impact of extreme financial losses that an organisation might have to encounter due to a sinful cybercrime but also strengthens the organisation's overall safety stance. | 7. Cybersecurity not only lessens the impact of extreme financial losses that an organisation might have to encounter due to a sinful cybercrime but also strengthens the organisation's overall safety stance. |
Importance of Network Security and Cybersecurity
Over the past few years, network security has been considered the highest priority for protecting commercial and residential networks. Wireless routers, which are present in the majority of households with high-speed internet connections, might be vulnerable if they are not adequately protected. Organisations and households can prevent the compromise of confidential data and delicate information by implementing strong security procedures.
Additionally, network security measures promote confidence and trust among stakeholders by creating a safe atmosphere for carrying out business activities and commercial transactions. In addition to providing asset protection, network security is essential for preserving business continuity and minimising any financial and reputational losses from security lapses. Hence, investing in robust network security is not only wise but also necessary for the long-term health and profitability of any organisation.
Our society is fundamentally more dependent on technology than it has ever been, and there are no signs that this tendency will reverse. This is the reason behind the tremendous increase in the demand for cybersecurity in the past few years. The availability, confidentiality, and integrity of information are critical in today’s globally networked society, where data flows nonstop. In the absence of strong cybersecurity protection, malevolent entities may take advantage of weaknesses in systems to compromise confidential information, steal vital functions, and cause disorder. Such breaches have consequences that go well beyond monetary losses and may also harm one’s reputation, erode trust, and even jeopardise national security. Furthermore, as technologies like the Internet of Things and artificial intelligence advance, the attack surface expands, which further helps us realise the importance of cybersecurity. As a result, making investments in cybersecurity is essential for promoting resilience, trust, and innovation in our digital environment.
Conclusion
To put it in a nutshell, network security and cybersecurity are sometimes used synonymously as they cover different but related areas when it comes to protecting digital assets. Network security is just one part of cybersecurity. In particular, network security is concerned with preserving the protocols and infrastructure that support data transmission and communication within networks. In contrast, cybersecurity has a wide range of services that are implemented to protect sensitive information from malicious cyber threats.
Hence, both are essential for thwarting constantly changing cyber threats and safeguarding the system against malicious activity, unauthorised access, and data breaches. Instead of creating an argument between cybersecurity and network security strategies, it would be a wise decision to implement both of these strategies to strengthen defences, reduce risks, and protect organisations and their sensitive information in an increasingly digitalised and linked world.









