
- jaro education
- 11, March 2024
- 10:00 am
The domain of cloud security is set to undergo transformative shifts in the year 2024. In this exploration, we will look into the emerging trends and predictions that are poised to shape the narrative of cloud security and will take a glimpse into cloud computing technology. Join us on this journey as we anticipate the key developments and strategies that will define the position of cloud security in this year.
Introduction to Cloud Security
Cloud security encompasses a comprehensive set of procedures, technologies, controls, and policies designed to protect cloud data, applications, and environments from various vulnerabilities and security threats. With the increasing adoption of cloud-based tools and digital transformation strategies, the significance of cloud security has become paramount. This multifaceted approach not only shields data but also aids organizations in adhering to regulatory compliances and safeguarding customer privacy.
Significance of Cloud Security in Modern Enterprises
In contemporary enterprises, there is a pervasive shift towards cloud-based environments and various computing models such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS). This transition, offering flexibility in infrastructure management and offloading IT-related tasks, brings forth numerous challenges for enterprises, particularly in the dynamic scaling of applications and services.
Table of Contents
As businesses increasingly migrate to the cloud, the most important concern is understanding the security requirements to protect data. While third-party cloud providers manage the infrastructure, organizations are still responsible for data asset security and accountability.Cloud security should be a top priority for any enterprise, as cloud infrastructure is critical to modern computing across a wide range of industries and verticals. Although cloud providers follow best security practices, organizations must consider and implement their own measures to protect data, applications, and workloads. The success of cloud adoption is dependent on the implementation of effective countermeasures to combat modern cyberattacks. Whether in a public, private, or hybrid cloud environment, implementing cloud security solutions and adhering to best practices is critical for ensuring business continuity and increasing an organization’s resilience to evolving threats.
Six Pillars of Robust Cloud Security
As organizations leverage cloud services from providers like Amazon Web Services (AWS), Microsoft Azure (Azure), and Google Cloud Platform (GCP), they must recognize that while these platforms offer native security features, the integration of supplementary third-party solutions is essential for achieving enterprise-grade cloud workload protection. The combination of a cloud-native and third-party security stack is vital for centralized visibility and policy-based granular control, ensuring adherence to industry best practices.
Here are the six pillars that ensure cloud security at its best.
1. Granular, Policy-Based IAM and Authentication Controls
Implementing Identity and Access Management (IAM) and authentication controls at a granular level are crucial for robust cloud security. Leveraging group and role-based approaches instead of individual IAM settings enhances flexibility, making it easier to adapt to evolving business requirements. Adopting the principle of least privilege ensures that groups or roles only possess the minimal access privileges necessary for their tasks. Enforcing strong IAM hygiene, including robust password policies and permission time-outs, further fortifies this pillar.
2. Zero-Trust Cloud Network Security Controls
Adopting a zero-trust approach to cloud network security involves deploying resources and applications in logically isolated segments within the cloud provider’s network. Utilizing technologies like Virtual Private Clouds (AWS and Google) or vNET (Azure) for isolation, along with subnet-based micro-segmentation, enhances security. Implementing dedicated WAN links in hybrid architectures and employing static user-defined routing configurations customizes access to virtual devices, networks, gateways, and public IP addresses, reinforcing this crucial pillar.
3. Enforcement of Virtual Server Protection Policies
Ensuring the enforcement of virtual server protection policies is vital for maintaining a secure cloud environment. Cloud security vendors offer robust Cloud Security Posture Management, automating the application of governance and compliance rules during virtual server provisioning. This includes auditing for configuration deviations and automatic remediation where possible, fostering a proactive and secure operational environment.
4. Safeguarding Applications with Next-Generation Web Application Firewall
Protecting applications, especially cloud-native distributed apps, requires a next-generation web application firewall (WAF). This WAF inspects and controls traffic to and from web application servers, automatically updating rules based on traffic behavior changes. Deployed in proximity to microservices running workloads, this pillar ensures granular control over application-level security, contributing to the overall robustness of the security framework.
5. Enhanced Data Protection
Enhanced data protection involves comprehensive measures such as encryption at all transport layers, secure file shares and communications, continuous compliance risk management, and maintaining good data storage resource hygiene. This includes identifying misconfigured storage buckets and terminating orphan resources, mitigating potential vulnerabilities and ensuring the integrity and confidentiality of data assets.
6. Threat Intelligence for Real-Time Detection and Remediation
Incorporating threat intelligence capabilities is essential for identifying and remediating both known and unknown threats in real time. Third-party cloud security vendors enhance context by cross-referencing cloud-native logs with internal and external data sources. This includes asset and configuration management systems, vulnerability scanners, and public threat intelligence feeds. Real-time alerts, coupled with AI-based anomaly detection algorithms, facilitate swift incident response, sometimes triggering auto-remediation workflows. This dynamic approach shortens the time to remediation and strengthens the overall security posture in the face of evolving cyber threats.
Types of Cloud Security Solutions
Cloud security solutions are diverse and continuously evolving to counter emerging threats. Some key types include:
- Identity and access management (IAM): It has centralized control over resource access, enabling policy enforcement across the organization.
- Data loss prevention (DLP): This type of cloud security solution provides visibility into stored data, automating discovery, classification, and de-identification of regulated data.
- Security information and event management (SIEM): It combines security information and event management for automated threat monitoring, detection, and incident response, often leveraging AI and ML technologies.
- Public key infrastructure (PKI): It manages secure information exchange via digital certificates, ensuring authentication and data confidentiality in cloud environments.
These solutions help organisations safeguard their cloud infrastructure and data from various security threats.
Top 10 Cloud Security Trends and Predictions Shaping 2024: A Comprehensive Overview
Anticipating the evolution from 2024 onwards, here are key observations and predictions that are made to shape the landscape of cloud security. These trends are set to redefine strategies and approaches, influencing the way organizations safeguard their cloud environments.
1. Integration of Artificial Intelligence (AI) as Standard
In the coming years, the integration of AI is set to become a cornerstone in cloud protection strategies. The deployment of self-learning algorithms capable of real-time threat anticipation and mitigation will be commonplace. We expect an industry-wide shift towards incorporating AI with vendors enhancing their offerings with similar capabilities. The trajectory set by pioneers like Check Point’s Threat Cloud is likely to inspire widespread adoption of AI-driven security measures.
2. Rise of Zero Trust Policies
The ‘never trust, always verify’ doctrine, encapsulated by Zero Trust policies, is predicted to gain prominence. More organizations are expected to adopt a security approach that grants access based on user behavior rather than relying solely on credential verification. As exemplified by Check Point’s longstanding commitment to this principle, adherence to Zero Trust principles is poised to become a standard practice among security vendors and cloud application architectures.
3. Evolution of Hybrid Cloud Security
The transition towards hybrid clouds will continue, necessitating comprehensive security measures across diverse data locations. The demand for a unified security platform that protects workloads and maintains security posture across on-premises, public and private clouds will grow. A shift towards integrated tooling, consolidating security solutions into one platform, will define the evolution of True Hybrid Multi-Cloud Application Protection Platforms.
4. Quantum Computing Risks<
As quantum computing advances, potential threats loom on the horizon. Protecting against these threats will require the development and implementation of advanced encryption methods and new security tooling and processes. While the significant impact may unfold beyond 2024, the development of solutions to counter quantum computing threats is expected to initiate serious consideration and planning in the coming years.
5. Cloud-Native Security Adoption
With a surge in cloud-native application development, security measures are expected to be ingrained from the inception of the development process. As per LinkedIn, the adoption of Cloud-Native Application Protection Platforms (CNAPP) like Check Point CloudGuard is projected to accelerate rapidly, becoming as commonplace as antivirus deployment by the year 2030.
6. Emphasis on Data Privacy
Stringent privacy regulations will drive the implementation of more rigorous security measures, placing a heightened emphasis on data privacy. Tools such as Data Security Posture Management (DSPM) will seamlessly integrate into corporate strategies as deployments simplify, ensuring compliance with evolving privacy standards.
7. Demand for Cloud Security Skills
The demand for professionals skilled in securing cloud environments is anticipated to surge. This growth will extend to Monitoring and Extended Detection and Response (XDR) service offerings from multiple Managed Security Service Providers (MSSPs) and Cloud Service Providers (CSPs), aligning with the evolving landscape of cloud security.
8. Increase in Multi-Cloud Adoption
Organizations embracing multiple cloud providers will seek skills to navigate the complexities of this landscape. The ability to secure multi-cloud deployments will become a sought-after skill, urging service providers to expand their practices to cover various cloud providers.
9. Growth in Managed Security Services
Outsourcing cloud security to specialized providers is expected to witness substantial growth. Organizations will leverage Managed Security Services to focus on their core business activities, mirroring the trend of outsourcing specialized services for operational efficiency.
10. Expansion of Cloud Security Automation
Automation will play a pivotal role in managing security alerts, updating patches, and conducting compliance audits. This trend is set to expand, freeing IT teams to concentrate on strategic tasks and reinforcing the integration of automation into cloud security practices.
The cloud security landscape in 2024 demands a proactive approach to emerging threats. By embracing these top trends, organizations can strengthen their security posture, mitigate risks, and navigate the complex and dynamic realm of cloud security effectively.
Cloud Security Challenges: Navigating the Complex Terrain
The challenges in the field of cloud security are as follows:
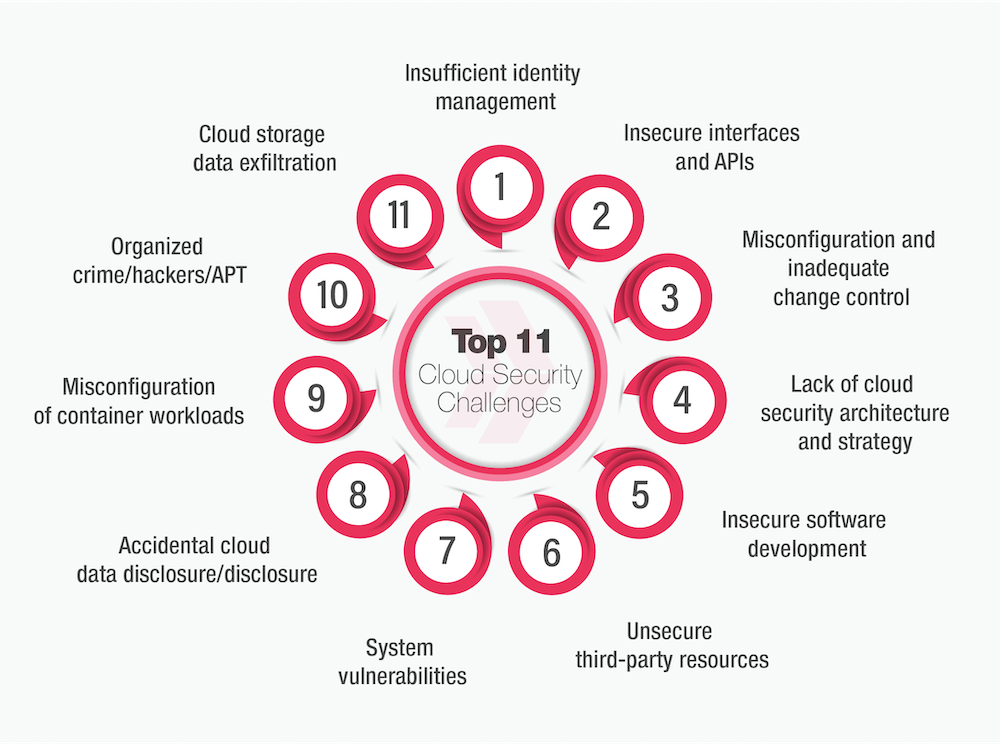
*clarusway.com
1. Lack of Visibility
Maintaining a clear understanding of how data is accessed and by whom poses a significant challenge in cloud environments. The decentralized nature of cloud services, accessed beyond corporate networks and through third parties, makes it easy to lose track of data interactions, necessitating robust visibility measures.
2. Multitenancy
Public cloud environments, accommodating multiple client infrastructures concurrently, introduce the risk of collateral damage. In the event of a malicious attack targeting one business, hosted services of others sharing the same environment may inadvertently get compromised, highlighting the challenge of multitenancy in cloud security.
3. Access Management and Shadow IT
While enterprises may effectively manage access points within on-premises systems, replicating the same level of control in cloud environments becomes a challenge. Unfiltered access to cloud services from various devices and geolocations, particularly in the absence of strict Bring-Your-Own-Device (BYOD) policies, poses a risk associated with access management and the emergence of shadow IT.
4. Compliance
Navigating regulatory compliance in public or hybrid cloud deployments proves challenging for enterprises. Despite using third-party solutions, ultimate accountability for data privacy and security remains with the enterprise. This complexity can lead to costly compliance issues, making it crucial for organizations to actively manage and ensure adherence to regulatory requirements.
5. Misconfigurations
Misconfigurations emerge as a prominent challenge in cloud security, with inadvertent insider actions contributing significantly to breaches. Examples include leaving default administrative passwords unchanged or neglecting to establish appropriate privacy settings, underscoring the importance of addressing misconfigurations in cloud computing environments.
Conclusion
Cloud security will bring forth both unprecedented opportunities and intricate challenges. From embracing AI-driven protection and Zero Trust policies to addressing multi-cloud complexities, organizations must adapt to these trends. Tackling challenges such as visibility, multi-tenancy risks, and misconfigurations is important for a resilient cloud security posture. As per recent trends, proactive strategies, skilled professionals, and improved automation emerge as key components for safeguarding the digital frontier.
In the era of digital transformation, as organizations shift to the cloud, the PG Certificate Programme in Cyber Security Management and Data Science equips mid to senior-level professionals with holistic cybersecurity expertise. Addressing cloud nuances, risk mitigation, and leadership skills, this course prepares them for evolving cyber trends and predictions in 2024.









