Digital-Forensics-Tools-and-Techniques-in-2025
Table of Contents

- jaro Education
- 18, July 2023
- 4:00 pm
In the modern, digital-first world, where cases of data breaches and cybercrimes are rising rapidly, digital forensics tools have never been more important. Whether following a hacker, discovering data theft, or acquiring evidence of a cyberattack, digital forensics tools experts rely on the best cyber forensic tools and techniques to do the job.
Whether you are a fan of cybersecurity, an information technology (IT) expert, or simply want to understand how law enforcement investigators track cybercriminals, this blog will explain all about forensic tools and techniques and methodologies in easy and conversational terms.
What Is Digital Forensics?
Digital forensics refers to the act of identification, preservation, analysis, and presentation of digital evidence. It is an essential field of cybersecurity that assists law enforcement and businesses in resolving digital crimes. The work entails a lot of computer forensics tools and techniques, whether it is recovering deleted files or tracking down unlawful network use.
Why Are Digital Forensics Tools Important?
Over 90% of modern crimes always leave a digital trail.
A global cost of cybercrime that exceeds 8 trillion dollars by 2025 (Source: Cybersecurity depends on Ventures).
85% of organizations suffer at least one incident of digital security every year (IBM Security Report).
Think of a crime scene, however, all the physical evidence, such as fingerprints, is replaced by log files, IP addresses, and metadata, among others. To acquire this type of data, digital forensic experts require specific forensic analysis tools, in order to acquire it successfully on computers, smartphones, or networks without making changes to the original evidence.
These aids assist in:
- Detection of security breaches
- Retrieval of lost/deleted information
- Gathering court case evidence
- The insider threat investigation
- Carrying out compliance audits
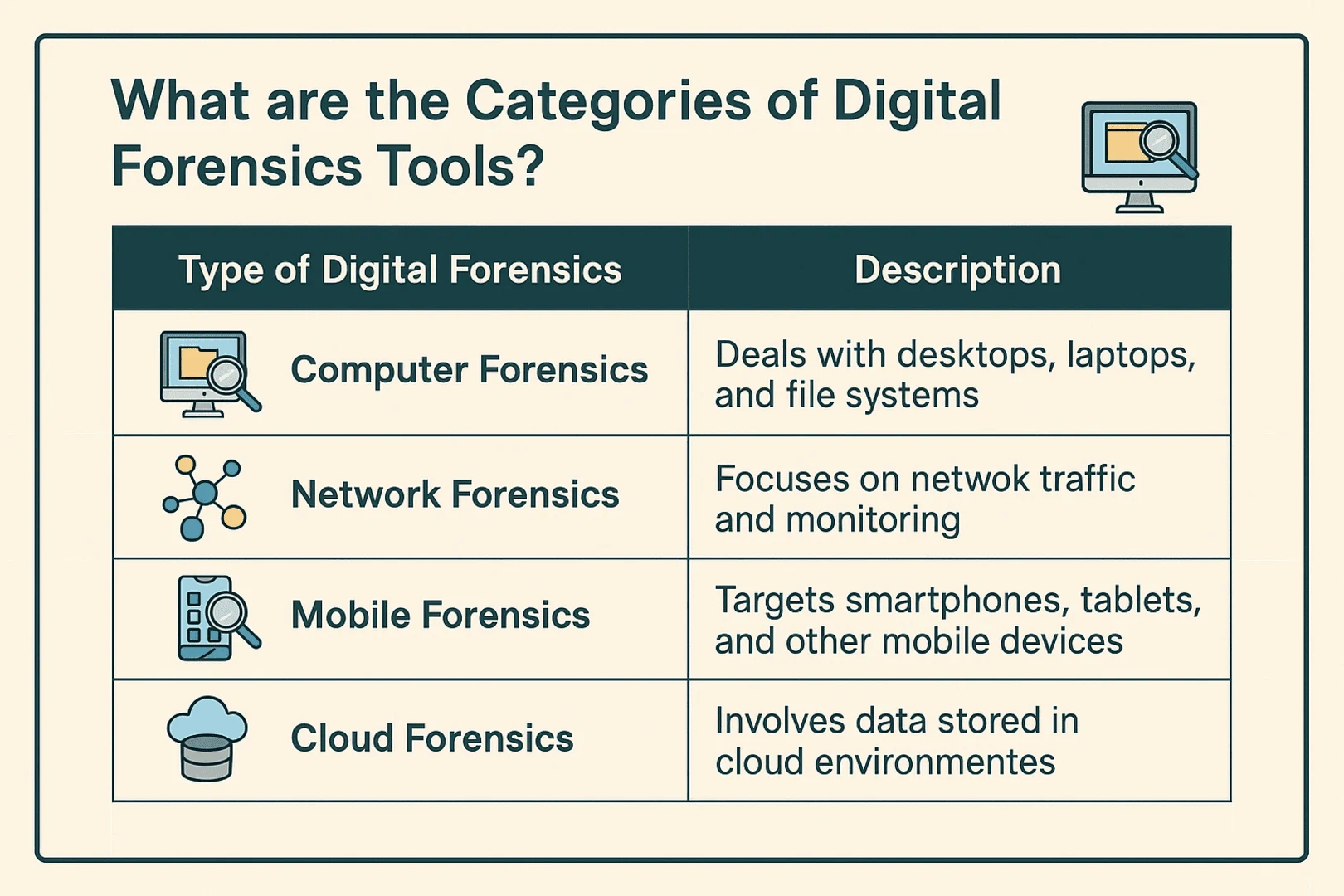
What are the Categories of Digital Forensics Tools?
Before we get into the tools, it is good to know that digital forensics touches upon several domains:
Top Digital Forensics Tools in 2025
As cyber threats evolve to become more advanced in 2025, digital forensics tools will also become more advanced, AI-powered, and cloud-ready. As a cybersecurity practitioner or a digital investigator, you should ensure that you keep up with the best tools. Friendly tour of the most popular digital forensics tools, causing a stir in 2018.
1. Volatility

*Medium
What it does: Volatility is a memory forensics framework (open-source) that assists an investigator in the analysis of RAM dumps to identify malware, rootkits, or system misbehavior.
What is new in 2025?
- The current flagship version is Volatility 3, which is reimplemented in Python 3 and has better modularity.
- It has also introduced AI-based plugin recommendation, which assists users in the auto-detection of the appropriate plugin for their memory images.
- It is now compatible with cloud-based memory acquisition, popular in forensic investigations in an AWS or Azure cloud.
Why it’s cool: It is lightweight, scriptable, and excellent at memory analysis during incident response.
2. Wireshark

*Medium
What it does: A network protocol analyzer (also called a packet sniffer) to capture and examine packets on a network in real-time.
What will be new in 2025:
Better deep packet inspection of more modern protocols such as QUIC and HTTP/3.
Integrated threat intelligence can be used to cause Wireshark to highlight packets that correspond to patterns of known bad traffic.
Support added: cloud sniffing, Remote packet analysis over secure APIs.
Popularity: It is required to analyze the network traffic when there is a breach or an intrusion.
3. EnCase

*Wikipedia
What it does: An effective forensic suite that is utilized in disk imaging, gathering evidence, and producing court-ready reporting.
What will be new in 2025:
- AI-assisted evidence tagging- automatically highlights suspicious documents, pictures, or file patterns.
- Quicker indexing with better SSD cache algorithms.
- Complete M1 / M2 Mac compatibility with forensic analysis of Apple devices.
Why it is a favorite: Law enforcement and enterprise investigators rely on it to acquire comprehensive, court-admissible evidence.
4. Autopsy

*autopsy.in
What it does: An open-source digital forensics platform that simplifies hard drive analysis with a user-friendly interface.
What’s new in 2025:
- New timeline analysis UI makes it easier to reconstruct user activity.
- Chat log and social media plugins updated for WhatsApp, Instagram, and Telegram (2025 versions).
- Cloud integration for AWS S3 and Google Drive artifact analysis.
Why it’s popular: It’s beginner-friendly and great for academic, corporate, or law enforcement use.
5. Cellebrite
*Cellebrite
What it does: A leading mobile forensics solution that extracts, decodes, and analyzes data from smartphones and tablets.
What’s new in 2025:
- Enhanced iOS 17 & Android 14+ support, including deleted data recovery.
- Cloud API integration lets you pull WhatsApp and Signal cloud backups (with legal access).
- Improved AI-based image and video classification—great for sorting through large media files.
Why it’s popular: It’s used worldwide for digital investigations involving mobile devices.
6. The Sleuth King

*SalvationDATA
What it does: A set of command line disk image and file system analysis tools.
2025: What is new?
- It has caught up with more recent Mac and enterprise storage technology, now supporting ZFS and APFS file systems.
- Analysis environments based on Docker are now accessible to repeatable investigations.
- Performance enhancement when analysing SSDs and NVMe storage.
Why it is famous: Best suited to technically minded analysts who like fine-grained control when examining a disk image.
7. Digital Forensics Framework
*DFF
What it is: Powerful digital evidence gathering and analysis suite, particularly on Linux machines.
2025: What is new?
- Includes a better modular plugin system with support to use custom analysis Python scripts.
- Modernized to allow multi-threaded analysis to speed up processing.
- Is now integrated with Elastic Stack to provide a centralized forensic data visualization.
What makes it popular: It is open-source and adaptable to investigators desiring to build out their own toolchain.
8. Magnet AXIOM
*Magnet AXIOM
What it does: An all-in-one solution to recovering and analyzing digital evidence on computers, smartphones, and in the cloud.
The novelty of 2025:
- Accelerating investigations through AI-powered artifact categorization.
- Enhancements to cloud analysis: More profound support of Slack, Teams, and Zoom extracting data.
- Teamwork dashboard to allow distributed teams to work on the same case.
Why it’s cool: It is self-explanatory and combines mobile, computer, and cloud analysis within one screen.
9. FTK Image
*HackNos
What it does: A light data preview and imaging utility applied in creating forensic disk images.
What is new in 2025:
- Feyling added ext4 and APFS file system support.
- Logging and auto-verification of the acquisition to claim tampering of the data.
- Field analysis: portable version extended to support USB live-boot.
Popularity: It is quick, trusted and is usually the initial stage in digital forensics.
10. Nagios
*MetriFire
What it does: Although it is not a digital forensics tool Nagios can assist in forensic preparedness by allowing networks to be monitored against suspicious activity.
What is new in 2025?
- Added behavioral anomaly detection plugin to detect deviation in the network activity baseline.
- Enhanced alerting by using machine learning-based threat correlation.
- Integration with SIEM platforms such as Splunk and QRadar to analyze log data in real time.
Why it made the list: It is proactive. Pre-breach detection and alerting so a breach can be investigated.
List of Most Powerful Digital Forensic Techniques
1. Digital Forensic Techniques
Digital forensics employs various techniques and tools to examine compromised devices. These techniques aid in uncovering hidden information, analyzing digital activity, detecting anomalies, and recovering deleted files. Here are some common techniques utilized in digital forensics.
2. Reverse Steganography
This involves uncovering hidden data within files by analyzing data hashing, which reveals changes in the underlying data structure.
3. Stochastic Forensics
It helps in investigating digital activity without digital artifacts, which is particularly useful for detecting insider threats and data breaches.
4. Cross-Drive Analysis
Professionals use this technique for correlating information across multiple drives to establish baselines and identify suspicious events.
5. Live Analysis
Live analysis helps in examining volatile data stored in RAM or cache while the device is running, typically conducted in a forensic lab to preserve evidence.
6. Deleted File Recovery
Recovering partially deleted files by searching for fragments spread across the system and memory.
These techniques play a crucial role in digital forensic investigations, providing insights into hidden information and reconstructing digital activities.
What Should One Consider in Choosing the Best Software for Digital Forensics?
- Parameters for Law Enforcement, Commercial Organizations, and Incident Response
Specific Needs of Different Industries: In law enforcement, compliance becomes the highest order of priority and becomes significant in evidence preservation. Data should be an insatiable need as far as efficiency is concerned in the commercial world, with incident response teams required to quickly find and fix vulnerabilities. Understanding the requisite unique features adequately will only help in selecting the right digital forensics and computer forensics software tools that coincide with company goals and regulatory standards.
- Scope: Individual Tools Vs. Suite of Tools
It’s your choice to choose from among a suite of tools or opt to buy them separately, depending on the jobs you want to accomplish. Individual programs can achieve everything, but a lot of the time it is easier and faster to string together several programs. A forensics software suite, on the other hand, is broader and can address several issues at the same time, thus making the process faster and easier during an investigation.
- Concerns about Privacy or Security
His primary confidentiality and security control means that most would keep the digitized material under examination. The selected digital forensics software should also prevent any subsequent unauthorized access to the data during equipment review. Always check for defensive features like encryption, authentication, and write protection that provide an extra degree of protection for the tool. Before making a purchase, ensure that the product has been thoroughly checked for safety shortcomings and conforms to all the standards and regulations.
- Open Source vs. Proprietary Tools: Expertise vs. User-Friendly
Although far more complicated and technical will most times be the understanding and practice required to maintain and update an open-source application, it will pay back that investment by being more flexible and tailored. Many proprietary systems, however, have intuitive interfaces and even provide one-on-one support to train users quickly to get started. Thus, many considerations would go into such a decision: what the team’s technical skill level is, whether any specific abilities are needed, and an openness to free or paid support.
- Costing: Open-Source Tools, Basic Suites, Large Organizations
The choice of tools depends largely on the available budget. While it is more often than not the case that open-source programs are free, one never finds using them effectively without considerable knowledge on the part of the user. Suites that have just the very basic features could often be cost-prohibitive for all but the smallest businesses. Businesses of some size could afford more advanced and featured suites with helpful extras for support. Cost, functionality, and return on investment are all factors to consider while determining the right tool.
Choosing the best digital forensics software requires careful evaluation of a number of factors. Matching the tool with business aims, security standards, user experience, and budget ensures efficient digital investigations and reliability in processes.
Jaro Education: Learning Without Limits
Career and Support Counseling
In addition to being one of the leading online higher education providers, Jaro Education offers its complete academic program along with career guidance and support counseling. Education is just one part of the growth toward human productivity; therefore, Jaro emphasizes the same on how to translate knowledge into professional success.
Personalized Career Guidance
This counseling service of Jaro intends to help working professionals, fresh graduates, and executive learners, all of whom go through career goal identification and planning the most suitable educational and professional strategies to achieve them. Counselors enable students to:
Understand strengths and areas for development
Draft short- and long-term career goals
Employ industry-relevant programs
Facilitate transitions into roles or up-skilling
Dedicated Student Support
All through enrollment and after completing the program, Jaro’s support teams will handle a one-on-one approach with students. This includes:
- Academic Advisors follow students’ progress through course completion
- Career Counselors conduct resume reviews and interview tips while providing market insights
- Technical Support to assist in ensuring a seamless digital learning experience
Bottom Line
Digital forensics tools and techniques play a crucial role in modern investigations, allowing experts to analyze electronic evidence and uncover vital information. As technology continues to evolve, these tools become increasingly essential in solving crimes, detecting cyber threats, and preserving evidence for legal proceedings.
Every aspect of this program is designed to meet the specific needs of organizations. It offers a holistic curriculum through interactive online learning and capstone projects to enhance knowledge and skills in cybersecurity.
Frequently Asked Questions
Digital forensics tools are software applications used to collect, analyze, and preserve data from computers, mobile phones, networks, or cloud platforms during investigations. These tools help in uncovering evidence related to cybercrimes, data breaches, or legal disputes.
With the rise of cyber threats, remote work, and cloud usage, digital forensics tools in 2025 are more advanced than ever. They help professionals identify security breaches, recover lost data, analyze digital evidence, and ensure organizations are compliant with cybersecurity laws.
There’s no single “best” tool—it depends on what you need. For memory analysis, Volatility is great. For mobile forensics, Cellebrite is a leader. If you want a full investigation suite, Magnet AXIOM or EnCase is ideal. Beginners often prefer Autopsy for its simple interface.
Yes! Some popular free and open-source tools include:
- Volatility (memory forensics)
- Autopsy (disk analysis)
- Wireshark (network packet analysis)
- The Sleuth Kit (TSK) (command-line forensic suite)
These tools are widely used by students, researchers, and professionals alike.
Yes, many digital forensics tools can recover deleted files unless they’ve been securely overwritten. Tools like FTK Imager, Autopsy, and EnCase are commonly used for file recovery during investigations.










6 thoughts on “Digital-Forensics-Tools-and-Techniques-in-2025”
Informative guide on digital forensics tools and techniques. Valuable resource for understanding investigative processes. Well-explained!
Thank you for your positive feedback on our digital forensics guide! Visit our site for more detailed information.
Fantastic post! The detailed breakdown of digital forensics tools and techniques is incredibly informative. Thanks for sharing this valuable resource!
We’re glad you found the post informative! Visit our site for more insights.
Informative article on digital forensics! The detailed breakdown of tools and techniques provides valuable insights into this critical field.
Excellent overview of digital forensics tools and techniques! The article provides valuable insights into essential methods for effective cyber investigations.