Interview Questions and Answers for Aspiring Cyber Security Professionals in 2024
Table of Contents

- jaro education
- 1, March 2024
- 10:00 am
Securing a position in Cybersecurity remains a formidable challenge, given its resilience in the face of economic downturns. The unyielding demand for Cybersecurity professionals is met with a surge in competition, necessitating aspiring candidates to distinguish themselves. To assist aspiring Cybersecurity professionals in cracking interviews confidently in 2024, we have curated a comprehensive compilation of some best cybersecurity interview questions and answers. This blog aims to equip individuals with the knowledge and insights needed to successfully crack the Cybersecurity interviews.
Cyber Security Interview Questions and Answers
Some of the best cyber security interview questions for freshers are as follows:
Q1. What is a Brute Force Attack, and How Can it be Prevented?
Some of the best cyber security interview questions for freshers are as follows:
- Password Length: Set a minimum password length, making it more challenging to crack.
- Password Complexity: Increase password complexity by incorporating alphanumeric characters, special characters, and a mix of upper and lower case.
- Limiting Login Attempts: Restrict the number of consecutive login failures. For instance, after three consecutive failures, temporarily block user access or implement additional authentication methods like email alerts or OTPs to thwart automated Brute Force processes.
Q2. What is Port Scanning?
Port Scanning is a technique employed to identify open ports and services available on a host. Hackers use this method to gather information for potential vulnerabilities, while administrators use it to verify network security policies. Common Port Scanning Techniques include:
- Ping Scan
- TCP Half-Open
- TCP Connect
- UDP
- Stealth Scanning
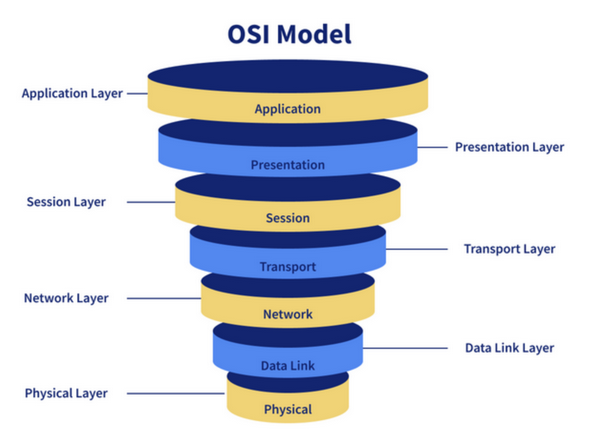
Q3. What are the Different Layers of the OSI Model?
The OSI (Open Systems Interconnection) model comprises several layers that guide communication over a network:
- Physical Layer : Transmits digital data through communication media.
- Data Link Layer : Handles data movement to and from the physical link, including encoding and decoding.
- Network Layer : Manages packet forwarding and routing paths for network communication.
- Transport Layer : Ensures end-to-end communication, splitting and passing data to the Network Layer.
- Session Layer: Controls connection, managing session initiation, termination, and synchronization between sender and receiver.
- Presentation Layer : Deals with presenting data in a proper format rather than raw datagrams or packets.
- Application Layer : Provides an interface between the application and the network, focusing on process-to-process communication.
*blog.knoldus.com
Q4. What is a VPN, and How Does it Work?
A Virtual Private Network (VPN) is employed to establish a secure and encrypted connection. In essence:
-
- Data from the client is sent to a VPN point, encrypted, and transmitted over the internet to another VPN point.
- At this point, the data is decrypted and sent to the server.
- Upon receiving a response, it undergoes encryption at a VPN point, is transmitted to another VPN point, decrypted, and finally sent to the client.
Q5. What is Cryptography?
Cryptography is the practice and study of techniques aimed at securing information and communication, primarily to safeguard data from third parties not intended to access it.
Q6. What is the Difference Between Symmetric and Asymmetric Encryption?
The differences between Symmetric and asymmetric encryption are as follows:
- Symmetric Encryption uses the same key for both encryption and decryption, enabling faster encryption but making it more vulnerable.
- Asymmetric Encryption employs different keys for encryption and decryption, resulting in slower encryption due to higher computation. Examples include Diffie-Hellman and RSA.
Q7. What is the Difference Between IDS and IPS?
The differences between IDS and IPS are as follows:
- IDS (Intrusion Detection System) detects intrusions, leaving the prevention to administrators.
- IPS (Intrusion Prevention System) not only detects intrusions but also takes proactive measures to prevent them.
Q8. Explain the CIA Triad.
The CIA triad consists of Confidentiality (ensuring data is only accessible to authorized personnel), Integrity (preventing unauthorized data modification), and Availability (ensuring data is accessible when needed).
Q9. How is Encryption Different from Hashing?
Encryption is reversible, allowing the conversion of encrypted data back to its original form through decryption. Hashing, however, is irreversible, making it impossible to revert hashed data to its original state.
Q10. What is a Firewall and Why is it Used?
A Firewall is a network security system positioned at system/network boundaries to monitor and control network traffic, safeguarding against viruses, worms, and unauthorized access.
Q11. What is the Difference Between VA (Vulnerability Assessment) and PT (Penetration Testing)?
The difference between VA (Vulnerability Assessment) and PT (Penetration Testing) is:
- Vulnerability Assessment identifies flaws in a target, with known weaknesses prioritized for fixing.
- Penetration Testing finds vulnerabilities on a target where all conceivable security measures are in place, testing for potential system/network breaches.
Q12. What is a Three-way Handshake?
A three-way handshake in a TCP/IP network is a method to establish a connection between a host and a client through a series of SYN, SYN-ACK, and ACK packets.
Q13. What are the Response Codes That Can be Received from a Web Application?
- 1xx – Informational responses
- 2xx – Success
- 3xx – Redirection
- 4xx – Client-side error
- 5xx – Server-side error
Q14. What is Traceroute? Why is it Used?
A traceroute is a tool revealing the path of a packet, listing the points (mainly routers) it passes through. It is used to identify connection issues and locate points of failure.
Q15. What is the Difference Between HIDS and NIDS?
- HIDS (Host IDS) monitors a specific host/device for suspicious activities.
- NIDS (Network IDS) monitors network traffic across all devices on the network.
Q16. What are the Steps to Set Up a Firewall?
Steps to set up a firewall include modifying default passwords, disabling remote administration, configuring port forwarding, addressing DHCP conflicts, enabling logging, and ensuring alignment with security policies.
Q17. Explain SSL Encryption
SSL (Secure Sockets Layer) is a security technology which establishes encrypted connections between web servers and browsers to protect data during online transactions.
Q18. What Steps Will You Take to Secure a Server?
Secure a server by ensuring strong passwords, creating new users for system management, removing remote access from default accounts, configuring firewall rules for remote access, and adhering to security policies.
Q19. Explain Data Leakage
Data Leakage involves the intentional or unintentional transmission of data from within an organization to an external, unauthorized destination. It can be prevented using Data Leakage Prevention (DLP) tools.
Q20. What are Some Common Cyber Attacks?
Common cyberattacks include Malware, Phishing, Password Attacks, DDoS, Man-in-the-Middle, Drive-By Downloads, Malvertising, and Rogue Software.
Q21. Explain the Concept of Public Key Infrastructure (PKI).
Public Key Infrastructure (PKI) is a cryptographic system facilitating secure communication over an insecure network. It utilizes a pair of keys, public and private, for encryption, decryption, digital signatures, and public key validation. Certificate Authorities (CAs) are employed to authenticate public keys, ensuring their legitimacy.
Q22. Are the Key Elements of a Strong Security Policy?
A robust security policy incorporates access control, encryption, regular updates, user training, incident response plans, and adherence to relevant regulations.
Q23. How Does a Rootkit Work and How Would You Detect It?
A rootkit is malicious software providing unauthorized access to a computer or network. Detection involves using specialized anti-rootkit tools and monitoring for anomalous system behavior.
Q24. Explain Cross-Site Scripting and SQL Injection.
Cross-site scripting (XSS) involves injecting malicious scripts into web applications, compromising user data. SQL Injection exploits SQL query vulnerabilities to manipulate databases. Both are forms of web application vulnerabilities.
Q25. What is a Zero-Day Vulnerability?
A Zero-Day Vulnerability is a security flaw undisclosed to the vendor, lacking a solution. Malicious actors can exploit it before a remedy is created.
Q26. Discuss the ISO 27001/27002 Standards.
ISO 27001 is a framework for Information Security Management Systems (ISMS), while ISO 27002 provides guidelines for implementing security controls and practices within an organization.
Q27. How Do Threat Detection Systems Work?
Threat detection systems monitor network traffic and system logs to identify suspicious activities or potential security threats using predefined rules and machine learning algorithms.
Q28. Explain the Principles of Ethical Hacking.
Ethical hacking involves testing systems for vulnerabilities to enhance security. Principles include obtaining proper authorization, maintaining confidentiality, and responsibly disclosing findings.
Q29. What are the Different Types of Network Security?
Network security includes perimeter security, firewall protection, intrusion detection systems, VPNs, and network segmentation to safeguard data and resources.
Q30. Discuss the Concept of Risk Assessment in Cybersecurity.
Risk assessment in cybersecurity involves identifying, assessing, and prioritizing potential threats and vulnerabilities to make informed decisions on security measures.
Q31. What is Incident Response, and How is it Managed?
Incident response involves a systematic strategy for handling and mitigating security incidents, encompassing phases such as preparation, detection, containment, eradication, recovery, and knowledge acquisition.
Q32. Explain the Principle of Least Privilege.
The Least Privilege principle restricts user and process access to the minimum required for their tasks, reducing the potential for unauthorized actions.
Q33. How Does Secure Socket Layer (SSL) Work?
SL ensures secure data transmission between web browsers and servers using encryption, authentication, and data integrity checks.
Q34. What is Network Sniffing?
Network sniffing is intercepting and analyzing network traffic to gather information, potentially for malicious purposes, or for monitoring.
Q35. Discuss the Importance of Disaster Recovery Planning in Cybersecurity.
Disaster recovery planning involves proactive preparation and responsive actions to safeguard against data loss or system failures, ensuring uninterrupted business operations.
Takeaway
Aspiring cybersecurity professionals in 2024 should be well-prepared for interviews with a solid understanding of evolving threats, technical skills, and an understanding of cybersecurity interview questions. Demonstrating problem-solving abilities, ethical considerations, and effective communication will distinguish candidates in this dynamic field, fostering success in the ever-changing landscape of cybersecurity.
If you want to expand your skillset further with valuable cybersecurity lessons, the PG Certificate Program in Cyber Security Management and Data Science gives you the ideal opportunity. You can join this course to dig deeper into useful cybersecurity skills through practical workshops led by expert business professionals. It offers a holistic curriculum that blends unique projects and case studies to comprehensively understand the subject matter. Plus, participants get ample opportunity for peer networking. With that, they can enrich their skills with hands-on workshops through experiential learning.








