Types of Cybersecurity Threats: From Malware to Phishing and Beyond
Table of Contents

- jaro Education
- 15, January 2025
- 11:00 am
Today, in the digital-first world, the more connected we get, the more distances a call is created. Nowadays, your threat is in the form of a cybersecurity threat: malicious attempts by hackers or cybercriminals to steal your data, destroy your devices, or disable services.
Any attempts to distinguish between different types of cyber threats in the working professional, the student, and the business owner constitute the first step toward self-protection in the cyber domain. This blog elaborates on the major types of cyber threats, the processes behind their realization and some handy tips along the way toward staying safe in the digital world with types of security threats.
So, without further ado, let us plunge in and put an end to whatever stands on the other side of your screens.
What are Cybersecurity Threats?
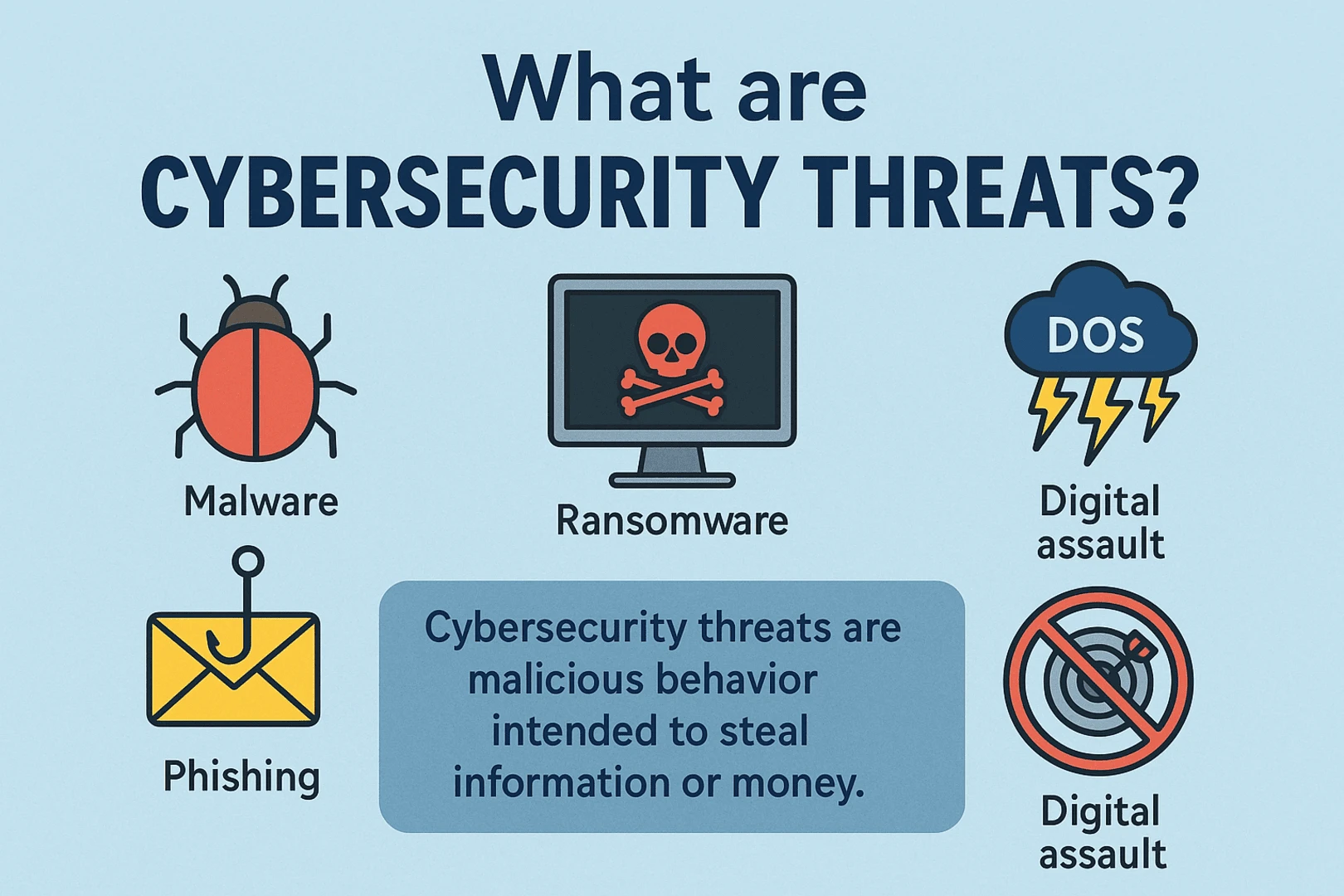
Cybersecurity threats are malicious behavior intended to steal information or money. This is done by interfering with computer systems, data, or corporate operations and digital life. Some of the most common examples of malware, ransomware, digital assault, phishing, denial of service (DoS) attacks, and numerous other attacks.
Cyber threats can lead to successful cyberattacks, and the consequences can be devastating for both individuals and organisations. Imagine unauthorised access to your sensitive information or a computer system crashing when you need it most. The fallout can include the theft of confidential data, significant financial losses, and disruptions to business operations. In some cases, these attacks can even pose physical risks. It’s crucial to understand these types of cybersecurity attacks and types of security threats to take proactive steps to protect yourself and your organisation!
7 Types of Cyber Security Threats
Nowadays, there are various types of cyber threats in the market that are used to steal people, money, data, and much more. So, let’s discuss some of the most common threats that you should be aware of:
1. Malware

*Malwarebytes
Malware, or malicious software, is one of the most common types of cyber threats, which are programmes designed to perform harmful tasks. It comes in various forms, each intended to achieve specific goals. For instance, malware can damage compromised computers, display harmful advertisements, and steal sensitive information.
Common forms of malware include:
- Cryptominers: This type of malware mines cryptocurrency on the victim’s computer.
- Mobile Malware: Software that targets mobile devices using various techniques, including social media networks, malicious apps, and SMS exploits.
- Infostealers: Malware that collects private information from a compromised computer and transmits it to the malware operator.
- Banking Trojans: Malicious programs that target financial data, including online banking login credentials.
2. Phishing Attacks

*Malwarebytes
Phishing attacks occur when an attacker sends emails that seem to come from trustworthy sources, aiming to obtain private information from the victim. These types of cyber threats combine social engineering with technology, as the attacker is essentially “phishing” for access to restricted areas by using the “bait” of a reliable sender.
The malicious actor might provide a link that directs you to a deceptive website designed to download malware or extract personal information.
You can prevent phishing attacks by carefully considering the types of emails you open and the links you click.
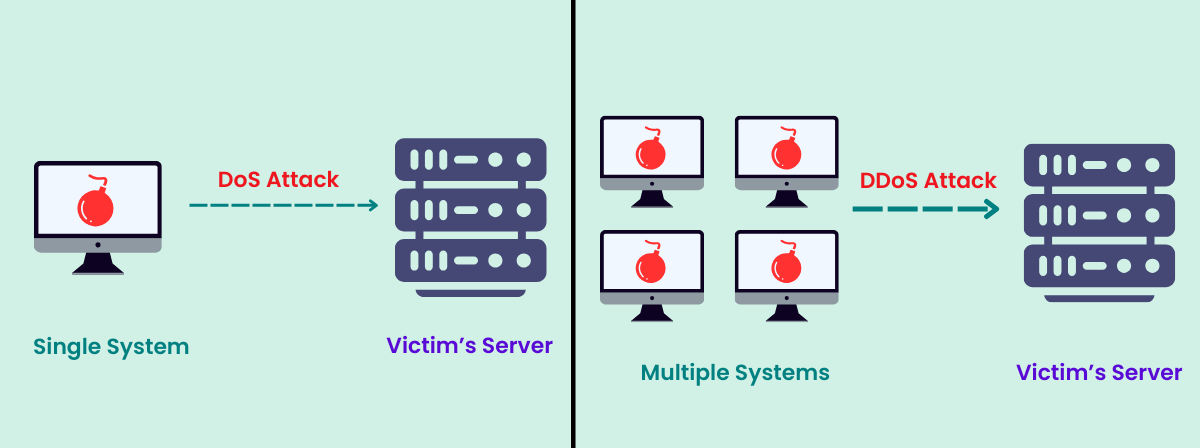
3. DoS and DDoS Attacks
*Indusface
A denial-of-service (DoS) attack uses one computer to overwhelm the target’s resources with traffic, rendering the system unable to respond to legitimate service requests. A distributed denial-of-service (DDoS) attack employs multiple malware-infected computers to achieve the same goal, depleting system resources to the point where actual users can no longer access them.
This is one of the most common types of cyber threats that bombard the target website with unauthorized requests, exhausting its resources until it can no longer assist visitors. This can lead to significant slowdowns or even a complete shutdown of the website.
Some of the DoS attack techniques include:
- HTTP flood: In this type of cyber threat, HTTP requests are used by attackers who appear legalised to swamp web servers. This is done to focus on a targeted system and to provide as many resources as possible on each request.
- ICMP Flood: In this type of attack in network security, the target is overloaded with ICMP Echo Request packets, using up both inbound and outgoing bandwidth. The system slows down because the servers are unable to handle the volume of requests, even if they may attempt to reply to each one with an ICMP Echo Reply packet.
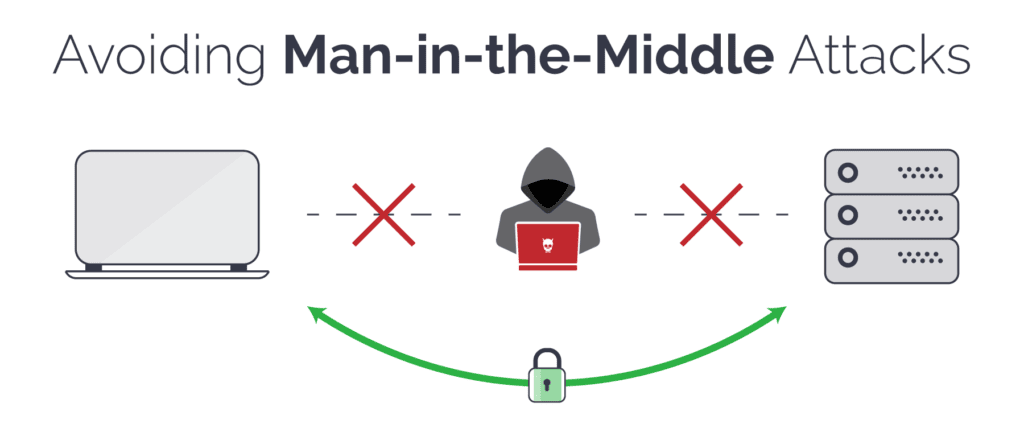
4. MitM Attacks
* Invicti
Man-in-the-middle (MitM) is another type of cyber threat that enables threat actors to intercept data moving between two parties, such as end users, computers, or networks. The attacker positions themself in the communication channel, allowing them to eavesdrop while the two parties remain unaware that someone else is listening or even altering messages before they reach their intended recipient.
Examples of MitM attacks include:
Wi-Fi Eavesdropping: In this type of cyber threat, an attacker creates a setup of a Wi-Fi network that people can connect to while impersonating a trustworthy entity, such as a company or a brand. The attacker may watch connected users’ activities and intercept data, including login credentials and payment card details, thanks to the bogus Wi-Fi.
Email Hijacking: When a hacker impersonates a trustworthy company, such as a bank, and uses that email address to trick consumers into sending money or sensitive information to the attacker. In this type of cyber threat, the user complies with what they believe to be bank instructions, but they are actually from the attacker.
5. Account Takeover
Account takeover (ATO) is the most trending type of cyber threat. It is the process by which a threat actor takes control of an online account using credentials that have been stolen. Data breaches, fraud, or identity theft could result from it. Credentials can be obtained by threat actors through a variety of assaults, including phishing scams, social engineering, and data breaches, or by buying them on the dark web.
Threat actors can also utilise bots that automatically try to access the websites, logging in with various usernames and password combinations until they find a list of validated credentials. This type of cybersecurity attack can misuse the account or sell these credentials to other actors.
6. Whale-Phishing Attacks
Whale-phishing types of cyber threats specifically target the “big fish” or “whales” of an organisation; typically, they are C-suite executives or other key decision-makers. These individuals often have access to sensitive information that could be valuable to attackers.
A targeted “whale” who downloads ransomware is more likely to pay the ransom to prevent further harm to their reputation or the organisation. To prevent types of cyber threat attacks, one should implement the same safeguards as regular phishing attacks, such as carefully reviewing emails and their attachments or links and remaining vigilant for unusual activity.
7. URL Interpretation
In URL interpretation attacks, attackers manipulate and fabricate specific URL addresses to gain access to the target’s personal and professional data. This type of attack, also known as URL poisoning, derives its name from the attacker’s understanding of the order in which a web page’s URL information needs to be structured. The attacker “interprets” this syntax to discover how to access areas they shouldn’t.
To execute a URL interpretation type of cyber threat, a hacker might guess URLs that could grant them administrator privileges or back-end access to a site. Once they reach the desired page, they can manipulate the site or gain sensitive information about its users.
What are Different Cybersecurity Solutions?
There are multiple cybersecurity tools used by organisations to prevent the above-mentioned types of threats. Some of the solutions are:
- Application security: It is used to identify software vulnerabilities during testing and development and to defend live applications against threats such as web application assaults, network attacks, and exploits of software flaws.
- Network security: It allows businesses to block, filter, or lessen dangers by keeping an eye on network traffic and spotting potentially harmful activity.
- Cloud Security: It identifies and addresses vulnerabilities and erroneous security configurations in public, private, and hybrid cloud infrastructures.
- Internet of Things (IoT) security: Sensitive information is frequently stored on connected devices, which are typically not built with security in mind. IoT security solutions aid in increasing IoT device visibility and security.
Are You Ready to Become a Cybersecurity Professional?
Cybersecurity professionals are in great demand today, and this demand will only continue to grow in the future. There is a diverse array of available career paths that are tailored to different skill sets and interests. These range from highly technical roles like auditing to ethical hackers and security engineers, who are on the frontline to prevent cyber threats.
So, if you want to kickstart your career in this rapidly evolving domain, the PG Certificate Programme in Cyber Security Management and Data Science at IIM Nagpur is the right choice.
This programme is designed for security leaders to navigate the complex world of cloud-based models, privacy, and risk management. This course offers essential cybersecurity knowledge, enabling systematic risk assessment and management with a focus on efficiency. Beyond technical knowledge, one can also enhance communication, leadership, team management and governance skills, ensuring a complete understanding of cybersecurity in today’s competitive job sectors.
Key Highlights of the Programme:
- Certificate of Completion from IIM Nagpur
- Live classes by highly experienced faculty from IIM Nagpur
- Holistic Curriculum— a blend of case studies, projects, etc.
- Hands-on workshops through experiential learning
- Jaro Education: Your Reliable Partner for Academic Success
Jaro Education is known as one of the renowned online higher education and upskilling companies, offering academic guidance and career counselling to individuals who want to build a thriving career. We are associated with some of the prestigious universities and schools to bring standard programs to suit diverse learning needs and professional aspirations, ensuring our students receive the best education and opportunities for growth in their fields.
Conclusion
Now, you must be informed about computer security attack types and how you can tackle them; you can not only protect yourself but also make your organisation a safe digital future. Embrace the challenge, and let your journey into cybersecurity begin!
If you’re interested in building a career in cybersecurity, the opportunities are wide. With the right industry certificate and educational background, you can successfully pave the path in this critical field. As the demand for cybersecurity personnel continues to grow, now is the right time to make a move into this rewarding career by enrolling in the PG Certificate Programme in Cyber Security Management and Data Science offered by IIM Nagpur.
Frequently Asked Questions
Cybersecurity threats are malicious activities or attempts that target digital systems, networks, or data. These threats can include hacking, phishing, malware, ransomware, and more, designed to steal, damage, or disrupt information and technology.
Some of the most common types include:
- Phishing
- Malware
- Ransomware
- Denial-of-Service (DoS) attacks
- Man-in-the-Middle (MitM) attacks
- Insider threats
- SQL Injection
- Zero-day exploits
Everyone is at risk, from individuals and students to businesses and large organizations. However, industries like finance, healthcare, and education are particularly targeted due to the sensitive data they handle.
You can stay safe by:
- Using strong, unique passwords
- Enabling two-factor authentication
- Avoiding suspicious links or downloads
- Keeping software and antivirus up to date
- Regularly backing up your data
A cybersecurity threat is the potential danger or vulnerability (e.g., a weak password), while a cyber attack is the actual act carried out by a hacker (e.g., stealing data using that weak password).










2 thoughts on “Types of Cybersecurity Threats: From Malware to Phishing and Beyond”
Great breakdown of cyber security threats! Your article offers a clear understanding of various risks and how to address them.
Thanks! That means a lot. Please keep following us more more relevant content.