What Is Network Security? Definition and Types

Table Of Content
- What Is Network Security?
- Types of Network Security
- Network Security Best Practices for Modern Organizations
- Old Thinking vs Modern Network Security
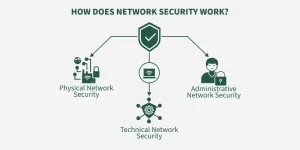
What Is Network Security?
*geeksforgeeks.org
By definition, network security refers to the policies, processes, and technologies used to protect a computer network and its data from unauthorized access, misuse, disruption, or destruction.
However, if you examine it through the lens of practice, then the meaning of network security is better understood as a continuous system of trust management, determining who and what is allowed to communicate, when, how, and under what conditions.
The key things it covers are:
- Devices are trying to connect
- Users requesting access
- Data moving across systems
- Applications talking to each other
Unlike point-in-time security measures, network security operates in motion, which means that the traffic flows, threats evolve, permissions change and the network must respond dynamically, without slowing business down.
In short, Network security ensures that the right traffic gets through, the wrong traffic stays out, and suspicious behavior gets flagged before damage is done.
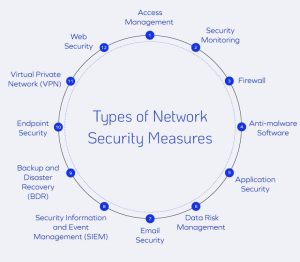
Types of Network Security
*dotsecurity.com
Network security is not a single technology. It’s an ecosystem. Below are the core types of network security, each solving a different problem but working toward the same goal: controlled, secure connectivity.
1. Firewall Security
Firewalls are the first line of defense and still one of the most critical. At a basic level, a firewall monitors incoming and outgoing network traffic and decides whether to allow or block it based on predefined rules.
But modern firewall security goes far beyond simple filtering. Today’s firewalls can:
- Inspect traffic at the application level
- Detect suspicious patterns
- Enforce organizational access policies
They don’t just ask where traffic is coming from. They ask what it’s trying to do.
2. Intrusion Detection and Prevention Systems (IDS/IPS)
Firewalls control access. IDS and IPS focus on behavior.
- Intrusion Detection Systems (IDS) monitor network traffic and flag suspicious activity
- Intrusion Prevention Systems (IPS) go a step further by automatically blocking detected threats
Together, they act as the network’s early warning system. If a firewall is the gatekeeper, IDS/IPS is the surveillance team that is watching continuously for anomalies that don’t fit expected patterns.
3. Virtual Private Networks (VPNs)
Remote work changed everything. When employees connect from outside the corporate network, VPNs create a secure, encrypted tunnel between the user and the organization’s systems.
This ensures:
- Data confidentiality
- Protection from interception
- Secure access over public networks
VPNs remain a cornerstone of network security, especially in distributed and hybrid environments.
4. Access Control and Network Segmentation
Not everyone needs access to everything. And not every system should talk to every other system. Access control enforces who can access what, based on identity, role, and context.
Network segmentation takes this further by dividing the network into isolated zones. If one segment is compromised, attackers can’t easily move laterally across the network. This principle, often called least privilege, dramatically limits the blast radius of breaches.
5. Wireless Network Security
Wireless networks introduce convenience and risk. Without proper controls, Wi-Fi can become an open door. This is where concepts like network security work.
A network security key is essentially a password or encryption key that authenticates devices before granting access to a wireless network. But strong wireless network security goes beyond passwords, here’s how:
- Encryption protocols
- Device authentication
- Monitoring unauthorized access points
In high-traffic or enterprise environments, wireless security is often one of the most targeted and most underestimated areas of network security.ok
Network Security Best Practices for Modern Organizations
While there is no such thing as a perfectly secure network. What exists instead are well-defended, well-observed, and well-adapted networks. And when talking about the best practices for network security it’s about knowing what’s happening, controlling access intelligently, and responding faster than attackers can move. This shift can be done through:
1. Adopt a Zero Trust Mindset
“Never trust, always verify” sounds simple. In reality, it’s a fundamental redesign of how networks think. Zero Trust assumes:
- No device is trusted by default
- No user is automatically safe
- No request is harmless just because it’s internal
Basically, each and every access request is evaluated based on identity, device posture, location, and behavior. This removes blind trust and replaces it with continuous verification.
2. Strengthen Authentication and Encrypt Everything That Moves
Passwords alone are no longer a security control. They’re a starting point. Effective network security combines:
- Multi-factor authentication (MFA)
- Strong encryption for data in transit
- Secure key management practices
The reason why this matters is because even if traffic is intercepted, encrypted data remains unusable. Attackers may get access but they don’t get value. That distinction is critical.
3. Treat Continuous Monitoring as a Core Capability
Security failures rarely happen instantly. Continuous monitoring allows organizations to:
- Detect unusual traffic patterns
- Identify unauthorized access attempts
- Spot lateral movement inside the network
This isn’t about watching everything manually. It’s about visibility, knowing what “normal” looks like so anomalies stand out immediately. No visibility means no control.
4. Run Regular Vulnerability Assessments
A network that was secure six months ago may already be exposed today. If you are wondering why, then here are a few reasons you must know:
- New devices get added
- Software updates introduce new gaps
- Attack techniques evolve faster than policies
Regular vulnerability assessments help uncover misconfigurations, outdated protocols and weak access controls. Think of this as preventive maintenance, not damage control.
5. Build Security-Aware Humans, Not Just Secure Systems
Here’s the uncomfortable reality: Most networks are breached through people, not technology. That’s why employee awareness is a network security control, not a soft skill. Effective programs focus on:
- Recognizing phishing attempts
- Understanding access responsibilities
- Knowing how to report suspicious behavior
A trained employee can stop an attack before it ever touches the network.
Old Thinking vs Modern Network Security
The table below shows how the mindset around network security has shifted, moving away from fixed defenses toward building smarter systems that can see, decide, and respond in real time.
| Traditional Network Security Thinking | Modern Network Security Approach |
| Trust anything inside the network perimeter | Verify every user, device, and request, inside or outside the network |
| Rely on static firewall rules | Use adaptive, context-aware access controls |
| Focus on preventing entry | Assume breaches can happen and limit their impact |
| Limited visibility after access is granted | Continuous monitoring throughout the session |
| Security is handled mainly by IT teams | Shared responsibility across systems, users, and processes |
| Designed for fixed offices and on-prem systems | Built for cloud, remote work, and mobile environments |
Common Network Security Threats You Should Be Aware Of
Now that we have a complete idea regarding network security, it’s equally important to understand what network security is actually defending against. Threats don’t announce themselves. They blend in, escalate quietly, and often exploit basic oversights.
Here are the most common ones organizations deal with today.
1. Malware and Ransomware
Malware is an umbrella term, but ransomware deserves special attention. Once inside a network, it encrypts data, locks systems, and demands payment for access.
The real damage?
- Operational downtime
- Loss of critical data
- Long-term reputational harm
And no, paying the ransom doesn’t guarantee recovery.
2. Phishing and Social Engineering
Not all attacks are technical. Some are psychological.
Attackers trick users into clicking malicious links or sharing credentials. Once inside, they move laterally through the network—often undetected for weeks.
This is why network security must assume users can make mistakes and design controls around that reality.
3. Insider Threats
Sometimes, the risk is already inside the network.
This can include:
- Disgruntled employees
- Accidental data exposure
- Misconfigured access permissions
Strong network security limits what insiders can access and monitors unusual behavior.
4. Distributed Denial of Service (DDoS) Attacks
DDoS attacks flood a network with traffic until it becomes unavailable. The goal isn’t data theft. It’s a disruption. For customer-facing platforms, even minutes of downtime can translate into massive losses.
Network Security vs Cybersecurity: Are They the Same?
Short answer: No. Long answer: Network security is a subset of cybersecurity. Let’s break it down for better clarity:
| Network Security | Cybersecurity |
| Protects network infrastructure | Protects all digital assets |
| Focuses on traffic and access | Covers applications, endpoints, data |
| Concerned with connectivity | Concerned with overall digital risk |
Network security answers questions like:
- Who can access the network?
- What traffic is allowed?
Cybersecurity zooms out and asks:
- How is data protected?
- Are applications secure?
- Are users trained?
You need both. One without the other creates blind spots.
How Jaro Education Supports Careers in Network Security and Cybersecurity?
For professionals looking to build or transition into cybersecurity roles, structured learning matters as much as technical curiosity. This is where Jaro Education plays a strategic role.
Jaro Education partners with leading universities and institutions to offer industry-relevant programs in cybersecurity, network security, and information security, designed specifically for working professionals. These programs focus not only on theory but also on real-world applications, covering areas such as network defence, risk management, security architecture, and incident response.
For anyone aiming to grow into roles such as network security engineer or cybersecurity specialist, these programs provide both credibility and career momentum.
So why wait any longer? Check them out right away!
Conclusion
Network security is no longer a background IT function, it’s a critical business capability and a fast-growing career domain. What once worked quietly in the background now demands constant attention, smarter decisions, and skilled professionals who can keep pace. For organizations, strong network security means continuity and trust. For individuals, it opens the door to roles that are both future-proof and genuinely impactful.
Frequently Asked Questions
Related Courses
Explore our programs
Find a Program made just for YOU
We'll help you find the right fit for your solution. Let's get you connected with the perfect solution.

Is Your Upskilling Effort worth it?
Are Your Skills Meeting Job Demands?
Experience Lifelong Learning and Connect with Like-minded Professionals








