Top Cloud Computing Interview Questions and Answers

Table Of Content
- Cloud Computing Interview Questions That You Must Master
- Conclusion
*upgrad
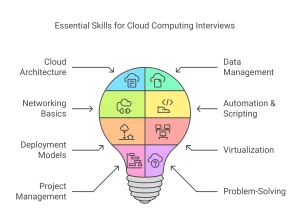
Cloud Computing Interview Questions That You Must Master
Part 1: Basic Cloud Computing Interview Questions and Answers for Freshers
These basic cloud computing interview questions cover the foundational knowledge every candidate must possess. Interviewers use these to confirm you grasp the core principles before moving to complex scenarios.
Q1. What exactly is Cloud Computing?
Answer: Cloud computing is the on-demand delivery of compute power, storage, databases, applications, and other IT resources over the internet. You pay as you go, eliminating the need to buy, own, and maintain physical data centers and servers.
- It offers services instantly and scalably.
- The fundamental concept is accessing shared resources remotely.
Q2. What are the key characteristics of Cloud Computing?
Answer: The National Institute of Standards and Technology (NIST) defines five essential characteristics:
- On-Demand Self-Service: Users can provision resources without human interaction.
- Broad Network Access: Capabilities are available over the network and accessed through standard mechanisms.
- Resource Pooling: Provider’s resources are pooled to serve multiple consumers using a multi-tenant model.
- Rapid Elasticity: Capabilities can be rapidly and elastically scaled outward and inward, often automatically.
- Measured Service: Usage is monitored, controlled, and reported, providing transparency for both the provider and the consumer.
Q3. Explain the three main Cloud Service Models (IaaS, PaaS, SaaS).
Answer: These models define the level of management control you retain versus the cloud provider.
| Model | What the User Manages | Example Services |
| IaaS (Infrastructure as a Service) | Operating System, Applications, Data | AWS EC2, Azure VMs, Google Compute Engine |
| PaaS (Platform as a Service) | Applications, Data | AWS Elastic Beanstalk, Azure App Service |
| SaaS (Software as a Service) | Nothing (Just Use It) | Salesforce, Microsoft 365, Gmail |
Q4. Differentiate between Cloud Computing and Virtualization.
Answer: Virtualization is the core technology that enables cloud computing. It allows one physical server to host multiple virtual machines (VMs). Cloud Computing is the delivery of those virtualized resources as a metered service over a network, usually the internet.
- Virtualization is a software concept (a technique).
- Cloud Computing is a service model (a business delivery mechanism).
Q5. What are the four major Cloud Deployment Models?
Answer: The four models dictate where the infrastructure resides and who manages it.
- Public Cloud: Services offered over the public internet by third-party providers (e.g., AWS, Azure, GCP).
- Private Cloud: Exclusive use by a single organization, managed internally or by a third party.
- Hybrid Cloud: A mix of public and private clouds, connected by proprietary technology that allows data and applications to be shared between them.
- Community Cloud: Shared infrastructure for specific organizations with common concerns (e.g., security, compliance).
Q6. Define “Multi-Tenancy” in the context of cloud.
Answer: Multi-tenancy is an architecture where a single instance of a software application or database serves multiple customers (tenants). Although tenants share resources, their data and business logic remain logically separate and isolated.
Q7. What is an Availability Zone (AZ) and how does it differ from a Region?
Answer: A Region is a geographical area where a cloud provider has its data centers, usually separated by hundreds of miles. An Availability Zone (AZ) is one or more distinct data centers within a Region, isolated from failures in other AZs.
- Regions ensure data sovereignty and latency.
- AZs ensure high availability and fault tolerance in a single Region.
Q8. What is Elasticity and Scalability in Cloud Computing?
Answer: This pair commonly appears in cloud computing interview questions and answers, so understanding the distinction is critical.
- Scalability is the ability to handle increased workload by adding resources over time, usually in anticipation of growth.
- Elasticity is the ability to automatically and rapidly provision or de-provision resources in response to immediate workload changes. It’s about automation and handling sudden spikes.
Q9. List the major Cloud Service Providers.
Answer: The market is dominated by the ‘Big Three,’ but others are significant:
- AWS (Amazon Web Services)
- Microsoft Azure
- GCP (Google Cloud Platform)
- Others
Q10. What is a Virtual Private Cloud (VPC)?
Answer: A VPC is a logically isolated section of a public cloud (like AWS or Azure) where you can launch resources in a virtual network that you define. It gives you control over your network environment, including IP address ranges, subnets, and network gateways.
Q11. How do you ensure Data Security in the Cloud?
Answer: Security relies on three main areas: encryption, access control, and the Shared Responsibility Model.
- Use encryption for data both at rest (in storage) and in transit (over networks).
- Implement strict Identity and Access Management (IAM) policies, granting the least privilege necessary.
- Adhere to the Shared Responsibility Model.
Q12. Explain the Shared Responsibility Model.
Answer: This appears frequently in cloud computing interview questions and answers for freshers, making it essential to remember.
| Responsibility | Cloud Provider (AWS/Azure/GCP) | Customer |
| Security OF the Cloud | Physical facilities, network infrastructure, hardware, and hypervisor. | Security IN the Cloud |
| Security IN the Cloud | Operating systems, applications, data, network configuration, and IAM. | Operating systems, applications, data, network configuration, and IAM. |
Q13. What is Load Balancing, and why is it essential?
Answer: Load Balancing automatically distributes incoming application traffic across multiple resources, such as virtual servers.
- It prevents a single server from becoming a bottleneck, ensuring high performance.
- It improves fault tolerance and availability by routing traffic away from unhealthy servers.
Q14. What are the advantages of Cloud Computing?
Answer: The primary benefits are financial and operational, like:
- Cost Savings
- Speed & Agility
- Scalability
- Global Reach
Q15. Define Cloud Storage and its types.
Answer: Cloud Storage is a model where data is maintained, managed, and backed up remotely and made available to users over a network.
- Object Storage (e.g., AWS S3): For unstructured data like files, images, and backups. Highly scalable and durable.
- Block Storage (e.g., AWS EBS): For structured data, typically used for the root volume of a virtual machine.
- File Storage (e.g., AWS EFS): Provides shared file access using protocols like NFS.
Part 2: Intermediate Cloud Computing Interview Questions
These intermediate cloud computing interview questions test your understanding of architectural components, security practices, and deployment models.
Q16. Explain Infrastructure as Code (IaC) and name a tool.
Answer: IaC is the practice of provisioning and managing your cloud infrastructure using code and configuration files rather than manual processes.
- It enables consistent, repeatable deployments and reduces human error.
- Terraform (multi-cloud) and AWS CloudFormation (AWS-specific) are popular IaC tools.
Q17. What is the role of the Hypervisor in Cloud Computing?
Answer: The Hypervisor (or Virtual Machine Monitor) is the software layer that creates and runs Virtual Machines (VMs).
- It allows a single physical server to host multiple isolated VMs.
- The cloud provider uses it to allocate resources (CPU, RAM, storage) to each tenant’s VM.
Q18. Compare AWS Lambda, Azure Functions, and Google Cloud Functions.
Answer: These are the Function-as-a-Service (FaaS) offerings, the backbone of Serverless Computing.
- AWS Lambda: Most mature, vast ecosystem integration.
- Azure Functions: Deep integration with the Microsoft ecosystem and development tools.
- Google Cloud Functions: Strong integration with Google’s data services and event triggers.
Q19. Describe the difference between Scalability and Elasticity in detail.
Answer: This is a crucial distinction. Scalability is typically a manual action and planned growth, like upgrading a server (vertical scaling) or adding more servers (horizontal scaling) to handle a predictable increase. Elasticity is automated and temporary, allowing a system to shrink back down when demand passes, thus optimizing costs. Mastering this topic is essential for all levels of cloud computing interview questions.
Q20. What is Vendor Lock-in, and how do you mitigate it?
Answer: Vendor lock-in occurs when switching providers is extremely difficult due to proprietary formats, services, or contractual issues.
- Mitigation: Use open-source standards (like Kubernetes or PostgreSQL), adopt a Multi-Cloud strategy, and utilize IaC tools (like Terraform) that are vendor-agnostic.
Q21. How do you implement High Availability (HA) for a web application?
Answer: HA requires designing the architecture to withstand a component failure.
- Deploy application instances across multiple Availability Zones (AZs) within a Region.
- Use a Load Balancer to distribute traffic and perform health checks.
- Use managed database services with automatic failover (e.g., AWS RDS Multi-AZ).
Q22. Explain the concept of ‘Cloud Bursting.’
Answer: Cloud bursting is a specific type of hybrid cloud deployment.
- A non-sensitive application runs primarily in a private cloud/data center.
- When demand peaks, the application automatically “bursts” into the public cloud to temporarily use its compute resources.
- It’s a cost-effective way to handle unpredictable traffic spikes without over-provisioning the private cloud.
Q23. What are Microservices, and why are they favored in the Cloud?
Answer: Microservices are an architectural style where an application is structured as a collection of small, independent services.
- They are favored because they align perfectly with cloud principles: independent deployment, better scalability, and resilience.
- If one microservice fails, the entire application doesn’t crash.
Q24. What is a CDN (Content Delivery Network), and what is its purpose?
Answer: A CDN is a geographically distributed network of proxy servers and their data centers.
- Its purpose is to cache content (images, videos, static files) at Edge Locations closer to the end-user.
- This significantly reduces latency and improves website loading speed and performance.
Q25. How do you approach Cloud Cost Management and Optimization (FinOps)?
Answer: FinOps is a cultural practice that promotes financial accountability.
- Rightsizing: Regularly identifying and downsizing underutilized resources (VMs, databases).
- Reserved Instances/Savings Plans: Committing to one- or three-year terms for predictable workloads to get steep discounts.
- Monitoring and Tagging: Using tools (like AWS Cost Explorer or Azure Cost Management) and tagging resources for clear cost allocation.
Q26. Explain the difference between Object Storage (e.g., S3) and Block Storage (e.g., EBS).
Answer:
- Object Storage (S3): Data is stored as objects with metadata, accessed via HTTP APIs. It’s highly durable, infinitely scalable, and best for backups and media files. It cannot run an OS.
- Block Storage (EBS): Data is stored as fixed-size blocks, accessed like a traditional hard drive. It’s necessary for the root filesystem of a VM and is required for installing an operating system.
Q27. What is Rate Limiting in the context of APIs and the Cloud?
Answer: Rate limiting is a strategy to limit the number of API requests a user or client can make in a given timeframe.
- It protects the application from DDoS attacks or abusive scripts.
- It ensures fair usage and prevents one client from monopolizing server resources, preserving performance for all users.
Q28. What are the key components of a Cloud-Native Application?
Answer: Cloud-native applications are designed from the ground up for the cloud environment.
- Containerized: Packaged using containers (Docker) for consistent deployment.
- Microservices: Decomposed into small, independent, loosely coupled services.
- Managed Services: Heavily reliant on PaaS and Serverless components.
- CI/CD Pipeline: Fully automated integration and deployment process.
Q29. Differentiate between Cloud Deployment and Cloud Migration.
Answer:
- Cloud Deployment: Launching a new application or service directly in the cloud environment.
- Cloud Migration: Moving an existing application, data, or IT workload from an on-premises data center to the cloud.
Q30. What is Data Sovereignty, and why is it a concern for global companies?
Answer: Data Sovereignty means that data is subject to the laws and regulations of the country in which it is processed and stored.
- It is a concern because a global company must ensure its data is stored in the correct Region to comply with local privacy laws (like GDPR in Europe).
Q31. What are the key pillars of the AWS Well-Architected Framework?
Answer: The framework provides guidance on designing and operating systems in the cloud. The five pillars are:
- Operational Excellence
- Security
- Reliability
- Performance Efficiency
- Cost Optimization
Q32. Explain the concept of Cloud Access Security Broker (CASB).
Answer: A CASB is a security enforcement point that sits between cloud consumers and cloud service providers.
- It ensures corporate security policies are extended to cloud services.
- It provides unified visibility, compliance checks, and threat protection for all SaaS, PaaS, and IaaS usage.
Q33. What are Security Groups (SG) and Network Access Control Lists (NACLs) in cloud networking?
Answer: Both are virtual firewall mechanisms, but they operate at different levels.
- Security Groups (SG): It acts as a virtual firewall for a single instance (VM or resource). They are stateful, meaning outbound traffic is automatically allowed for established inbound connections.
- NACLs: Acts as a firewall for an entire subnet. They are stateless, requiring explicit rules for both inbound and outbound traffic.
Q34. How do you design for Fault Tolerance in the database layer?
Answer: Fault tolerance ensures a system continues operating even when a component fails.
- Use Multi-AZ deployments with synchronous replication for immediate failover.
- Employ Database Sharding (splitting a database into smaller, separate pieces) to isolate failure domains and improve performance.
Q35. When would you choose PaaS over IaaS?
Answer: You choose PaaS when your priority is speed and reducing management overhead.
- PaaS is ideal for rapid application development (DevOps) because you skip managing the OS, patching, and middleware.
- You choose IaaS only when you need maximum control over the operating system and infrastructure environment.
Part 3: Advanced Cloud Computing Interview Questions
These cloud computing interview questions focus on strategy, optimization, and advanced architecture.
Q36. What is Serverless Computing and what are its drawbacks?
Answer: Serverless computing (often FaaS) is a model where the cloud provider fully manages all server logic. You only pay when your code executes.
- Drawbacks: Vendor lock-in is high; Cold Starts (initial latency when a function runs for the first time) can be a concern; and complex debugging can be difficult due to limited access to the underlying OS.
Q37. Compare the container orchestration tools: Kubernetes (K8s) vs. ECS vs. Azure Container Apps.
Answer: Kubernetes (EKS/GKE/AKS) is the open-source industry standard for complex, multi-cloud deployments, offering immense flexibility. AWS’s ECS (Elastic Container Service) is simpler, lighter, and deeply integrated with the AWS ecosystem. Azure Container Apps offers a serverless container environment, focusing on simplicity and microservices integration.
- Choose Kubernetes for maximum control and portability.
- Choose ECS or Azure Container Apps for simplicity and tighter platform integration.
Q38. How do you handle a sudden, unexpected spike in traffic using cloud features?
Answer: This requires a combined approach using Elasticity and Load Balancing.
- Auto Scaling: The load balancer detects the traffic increase, triggering the Auto Scaling Group (ASG) to provision new application instances.
- Caching: Ensure a CDN (like CloudFront) is in front of the application to absorb the bulk of the traffic for static content.
- Database Throttling/Scaling: Use read replicas and read/write splitting to prevent the database from becoming the single point of failure.
Q39. Explain Data Lakehouse Architecture and its relation to the cloud.
Answer: The Data Lakehouse is a new architecture that combines the flexibility and low cost of a Data Lake (for unstructured data) with the structure and governance of a Data Warehouse.
- Cloud object storage (S3, Azure Blob, GCP Storage) is the foundation, providing cheap, infinite storage for the lake.
- This architecture enables real-time analytics and machine learning directly on the vast amount of raw data.
Q40. Define Zero Trust Architecture (ZTA) and how you implement it in the cloud.
Answer: ZTA is a security framework that asserts no user, device, or system, inside or outside the network is trusted by default. “Never trust, always verify.”
- Implementation:
- Micro-segmentation: Isolate every workload and resource.
- Least Privilege: Grant access based on the bare minimum required (JIT – Just-in-Time Access).
- MFA & IAM: Enforce strict Multi-Factor Authentication for every access request.
Q41. You’ve noticed your cloud bill has doubled. What is your step-by-step approach to diagnosing and fixing the issue?
Answer: A common scenario question that tests your FinOps knowledge.
- Identify the Spike: Use the Cost and Usage Report (e.g., AWS CUR) to pinpoint the exact service and resource causing the increase (usually Compute, Networking, or Data Transfer).
- Resource Tracing: Check audit logs (CloudTrail, Azure Activity Log) to see who launched the resource and when.
- Optimization: Determine if the resource can be downsized (Rightsizing) or if it can be replaced by a cheaper service (e.g., an EC2 instance to a Serverless function).
- Automation: Implement automated shutdown schedules for non-production resources.
Q42. How do you achieve Data Consistency in a distributed cloud environment?
Answer: Consistency is challenging in distributed systems.
- You must trade off consistency for availability and performance (the CAP Theorem).
- Use managed services like Amazon DynamoDB (eventual consistency for high availability) or Amazon Aurora (strong consistency via synchronous replication) based on application requirements.
Q43. What is a Service Mesh (e.g., Istio), and why is it used with Kubernetes?
Answer: A Service Mesh is a dedicated infrastructure layer for handling service-to-service communication.
- It manages network traffic, security (mTLS), and observability between microservices.
- It is used with Kubernetes to offload complex networking and security logic from the application code, allowing developers to focus on business logic.
Q44. Differentiate between Durability and Availability in Cloud Storage.
Answer: This distinction is critical for cloud computing interview questions and answers.
- Durability: The guarantee that data will not be lost (e.g., 99.999999999% durability in S3). It relates to data preservation and integrity.
- Availability: The guarantee that the data will be accessible when requested (e.g., 99.99% availability). It relates to uptime and accessibility.
Q45. How does Encryption at Rest work in a Cloud Database service (e.g., RDS or Azure SQL)?
Answer: Encryption at rest involves using a key management service (KMS).
- The customer provides or generates a key in the KMS.
- The database service uses this key to encrypt the underlying storage volumes, backups, and snapshot data.
- Data is decrypted only when accessed by an authorized user or application, ensuring that the physical files are unreadable if stolen.
Q46. What is the difference between a Private Cloud and a Virtual Private Cloud (VPC)?
Answer:
- Private Cloud: An organization’s own, self-managed data center and resources, running their own cloud software. It uses single-tenant infrastructure.
- VPC: A virtual, logically isolated network partition within a Public Cloud provider’s infrastructure. It uses multi-tenant infrastructure but provides logical isolation.
Q47. Explain the importance of a CI/CD Pipeline in a Cloud Environment.
Answer: Continuous Integration/Continuous Deployment (CI/CD) automates the entire software release process.
- Speed: Enables faster delivery of features and bug fixes.
- Reliability: Ensures code is consistently tested and deployed, reducing human error.
- Cloud Alignment: Seamlessly integrates with IaC tools and container orchestration (Kubernetes) for fully automated, immutable infrastructure updates.
Q48. When would you advise a client to use a Multi-Cloud strategy?
Answer: Multi-cloud is using services from two or more public cloud providers (e.g., AWS and Azure).
- Risk Mitigation: To avoid the high risk of vendor lock-in or to achieve disaster recovery across platforms.
- Best-of-Breed: To use a provider’s specialized service, such as GCP for ML/BigQuery while keeping core compute on AWS.
- Geographic Compliance: To meet specific regional data sovereignty requirements that one provider cannot fully satisfy.
Q49. What is Edge Computing, and how does it relate to the Cloud?
Answer: Edge computing processes data physically closer to the source where the data is created, rather than sending it all back to a central cloud data center.
- Relation: The Edge acts as an extension of the Cloud. The Cloud manages the central control, storage, and long-term analytics, while the Edge handles low-latency processing and filtering for devices like IoT sensors.
Q50. Describe the steps you would take to design a Highly Scalable and Cost-Optimized cloud architecture for an e-commerce platform.
Answer: This is a system design question, requiring the synthesis of all knowledge.
- Decouple: Use a Serverless/Microservices architecture (FaaS, API Gateway) to keep components independent.
- Compute: Utilize Auto Scaling Groups with Spot Instances for non-critical/batch workloads to cut costs.
- Data: Use CDN for all static assets. Implement a managed, scalable database (e.g., DynamoDB or Aurora Serverless) with a caching layer (e.g., Redis) in front of it to handle read traffic spikes.
- Deployment: Use Infrastructure as Code (IaC) for automated, repeatable deployment across multiple AZs.
- FinOps: Implement tagging and Reserved Instances for the predictable database and core compute instances.
Conclusion
Your preparation with these comprehensive cloud computing interview questions and answers is the clearest indicator of your readiness to lead in the digital era. But securing those top-tier roles often requires formal validation of your expertise.
At Jaro Education, we recognize the escalating demand for highly skilled cloud professionals. We offer upskilling courses and executive programs designed specifically for those aiming to break into this dynamic field, accelerate their career growth, and master the complex architectures that drive modern business.
Invest in your knowledge, demonstrate your mastery of these concepts, and partner with us to solidify your expertise!
Frequently Asked Questions
Cloud computing interview questions typically explore your understanding of service models, deployment frameworks, and security considerations. Expect scenario-based problem-solving to evaluate real-world implementation knowledge.
Find a Program made just for YOU
We'll help you find the right fit for your solution. Let's get you connected with the perfect solution.

Is Your Upskilling Effort worth it?
Are Your Skills Meeting Job Demands?
Experience Lifelong Learning and Connect with Like-minded Professionals

